Cyber Threat Intelligence
Cyber Threat Intel Analysts are there to advise on what the best defence against the attacker(s) is. Cyber security is nearly always a defensive activity. You are essentially studying people, through the medium of technology. CTI is at its core, a structured analysis of the threat. Insight an organisation uses to understand the threats that they face. The insight is used to mitigate the harm that an adversary might inflict.
Indicators of Compromise
Indicators of compromise are pieces of forensic data, such as data found in system logs entries or files, that identify potentially malicious activity on a system or network.
Cyber Threat
A person or thing with the ability to inflict damage onto a victim.
A threat is a statement indicating the will to cause harm to or create some other kind of negative consequences for someone.
Many threats involve a promise to physically harm someone in retaliation for what they have done or might do. Some threats are simply meant to intimidate, and don’t involve pressuring someone to do something. Not all threats involve violence.
A security threat is someone or something that might make a situation unsafe.
Threat can also mean a warning or sign that harm or trouble is coming.
The word ‘cyber’ carries the following connotations:
- A relationship with modern computing (i.e., the digital age). (For example, early computers and home PCs from the 80s and 90s do not attract the term ‘cyber.‘)
- A relationship with the cutting edge of modern technology. (For example, IT security sounds more routine than cyber security, which implies a guard against the latest attack types.)
What does ‘Intelligence’ mean?
There is no agreed definition or model of intelligence. By the Collins English Dictionary, intelligence is ‘the ability to think, reason, and understand instead of doing things automatically or by instinct’. By the Macmillan Dictionary, it is ‘the ability to understand and think about things, and to gain and use knowledge’.
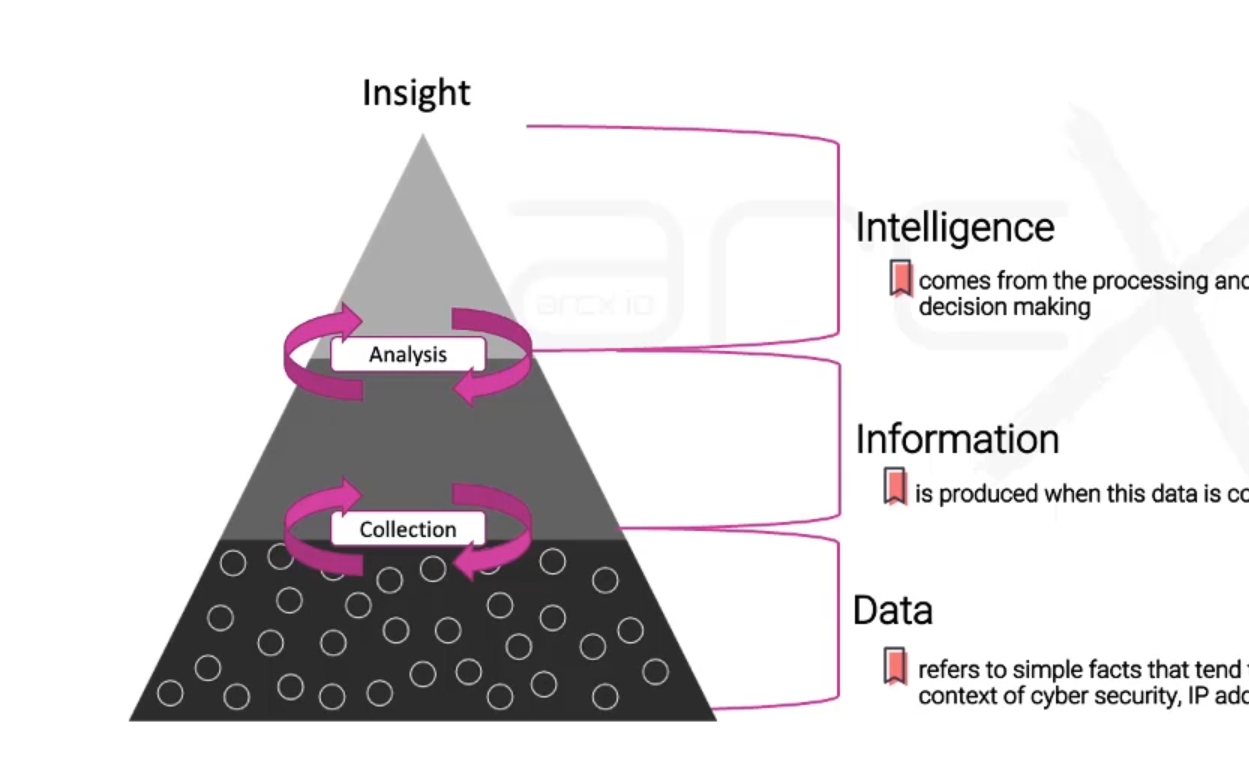
Intelligence - within the context of cyber security - describes the practice of collecting, standardising and analysing data that is generated by networks, applications, and other IT infrastructure in real-time, and the use of that information to assess and improve an organisation’s security posture.
The Stuxnet Computer Worm: Harbinger of an Emerging Warfare Capability
During the video, you may have heard Stewart mention an attack on an Iranian nuclear power plant.
We will be covering threat actors and the like in a later section of the course but for those of you who are interested in learning more about this specific attack, you can download a fantastic paper on it here.
The paper was produced in 2010 by Paul K. Kerr, John Rollins and Catherine A. Theohary as part of the Congressional Research Service and is titled, The Stuxnet Computer Worm: Harbinger of an Emerging Warfare Capability

Cyber threat intelligence is an area of cyber security that focuses on the collection and analysis of information about current and potential attacks that threaten the safety of an organisation or its assets.
Through the implementation of this tactic, organisations can take proactive steps to ensure that their systems are secure. By using cyber threat intelligence and analysis, data breaches and other issues can potentially be prevented, saving your organisation the significant financial costs of having to set any incident response plans in motion.
The purpose of cyber threat intelligence is to give organisations an in-depth understanding of the threats that pose the greatest risk to their infrastructure and devise a plan to protect their day-to-day business. CTI Analysts strive to provide as much actionable intelligence as possible.
Through the process of analysis, you can develop an understanding around why a threat actor may attack your systems to begin with. Knowing the opposition’s motive can shed light onto what areas of your systems could be the most vulnerable.
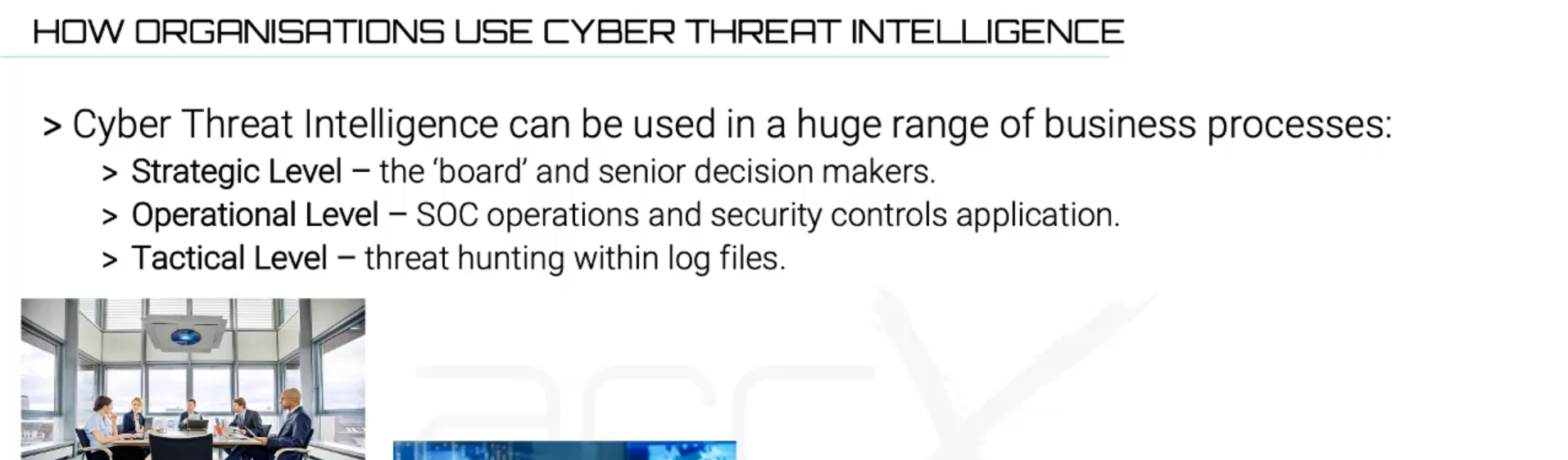
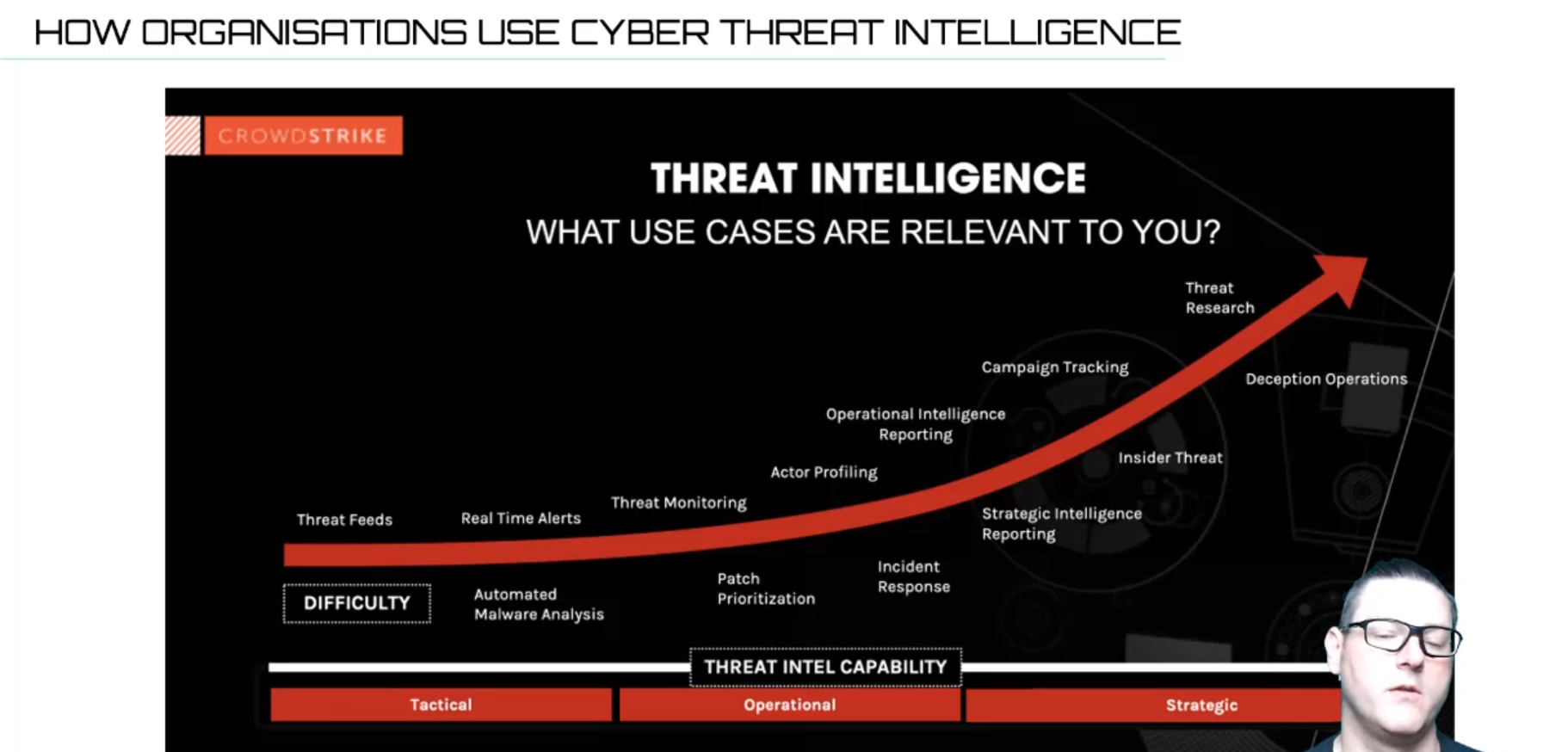
To round off this recap we want to highlight some of the key reasons that organisations use cyber threat intelligence:
- Identify and assess potential threats to their networks and systems.
- Enhance their overall security posture by proactively taking measures to prevent attacks.
- Improve incident response efforts by having up-to-date information about known threats.
- Prioritise resources for the mitigation of high-risk vulnerabilities.
- Monitor external sources for signs of a potential breach or attack.
- Stay informed about the tactics, techniques, and procedures used by malicious actors.
Role of a CTI Analyst
Cyber threat intelligence analysts gather data to track, evaluate, and report on threats that could have an impact on an organisation. They do this by combining contextual knowledge of the whole threat landscape with analytical abilities.
Analysts combine a variety of sources, including private data collections and open source intelligence (OSINT) evaluation, to produce a complete picture of an organisation’s risk posture that informs the steps the business takes to mitigate these risks.
They create short-term and long-term evaluations to help security teams better understand the threats they face and what they can do to prevent attacks and breaches in the future.
As mentioned in this short video, we consider the goal of an analyst to be the creation of insight through the combination of the art, craft and the science of CTI.
The roles and responsibilities of a CTI Analyst typically include:
- Identifying organisational intelligence requirements
- Collecting relevant data and conducting all-source analysis to inform decision making process
- Identifying, monitoring, and assessing potential threats or weaknesses
- Validating that security qualifications and requirements are met
- Creating reports that highlight key findings for security teams and other members of the organisation
- Presenting findings to other teams and proposing counteractions to mitigate threats