Intelligence Cycle
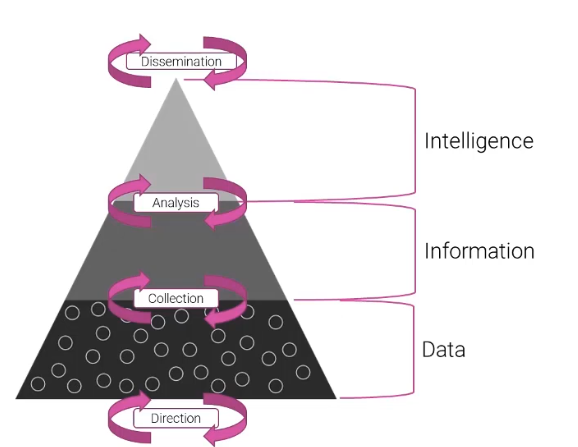
DATA -⇒ INTELLIGENCE
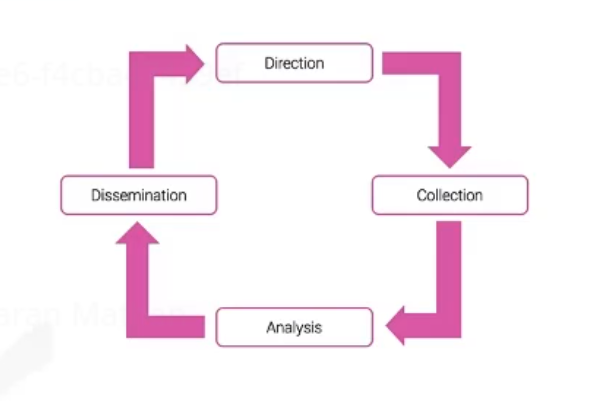
4 Steps
- Direction → Intelligence team takes direction from customer - Intelligence Requirements
- Collection → Intelligence team collects data and turns into information - tasking to sources and agencies (SandA)
- Analysis → Information is turned into Intelligence
- Dissemination → Intelligence is handed back to the client, which in turn stimulates new Direction…
Core of CTI
The intelligence cycle is at the core of cyber threat intelligence because it provides a structured framework for collecting, processing, analysing, and disseminating information about potential cyber threats. The intelligence cycle and its steps can be communicated in different ways dependent on who you speak with but some of the key elements that everyone can agree with sit below:
- Defining what information is needed to support decision-making and security operations.
- Gathering data from various sources, such as open source intelligence (OSINT), proprietary databases, and sensor networks.
- Converting raw data into usable information by verifying, validating, and fusing it into a coherent picture.
- Assessing the significance of the information and identifying patterns, trends, and potential threats.
- Sharing the results of the analysis with stakeholders who need it to make informed decisions and take appropriate actions.
- Using the results of the analysis to inform future collection and analysis efforts, as well as to validate the accuracy and reliability of the information.
By following this structured process, organisations can ensure that they have a complete and up-to-date understanding of the cyber threat landscape, and can take effective steps to protect themselves from potential threats.
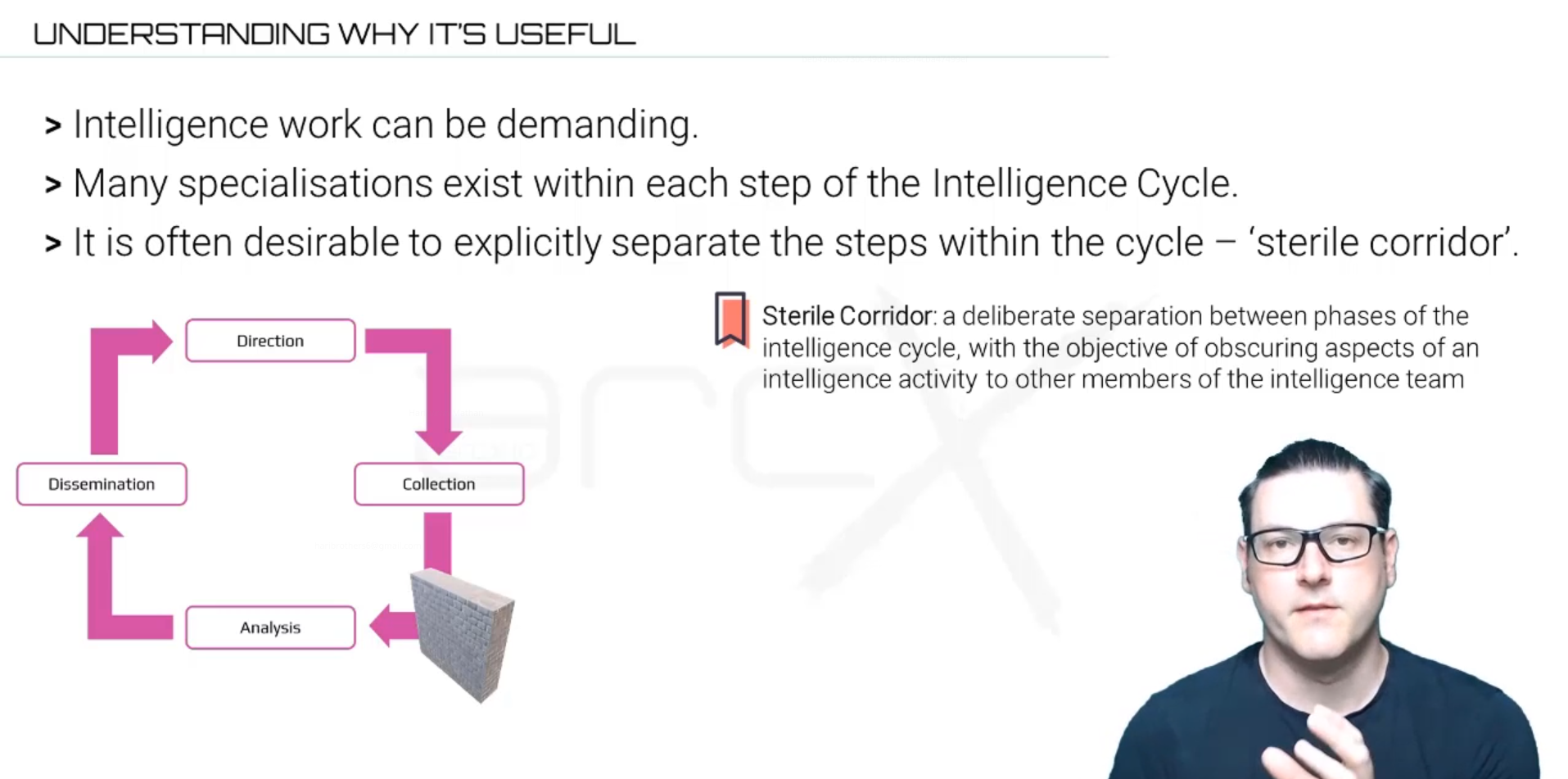
Sterile Corridor in Action:
-
Recruitment and Communication (Collection Phase):
- The asset uses a secure and untraceable method to deliver documents, such as a dead drop in a predetermined location monitored discreetly by operatives.
- To ensure the sterile corridor, communication is conducted through encrypted channels or a secure mobile app designed for covert messaging, ensuring no traceable link to either party.
-
Transporting the Documents (Processing Phase):
- Once collected, the documents are transferred through secure couriers or encrypted digital uploads to prevent interception by adversaries. The courier follows a carefully planned route avoiding known surveillance zones (physical sterile corridor).
-
Analysis in Headquarters (Analysis Phase):
- At the agency’s headquarters, the documents are analyzed in a compartmentalized intelligence unit. Only select analysts with the highest clearance access the files, ensuring the sterile corridor limits potential insider threats.
-
Dissemination to Decision-Makers (Dissemination Phase):
- The findings are summarized in a secure report and delivered to national security advisors using encrypted files or briefed in a soundproof room, ensuring no electronic surveillance or leaks.
-
Safe Extraction of the Asset (Operational Planning):
- If the asset needs to escape, a sterile corridor could involve arranging an exfiltration route using non-detectable vehicles or fake identities to avoid suspicion.