Sniffer Mode
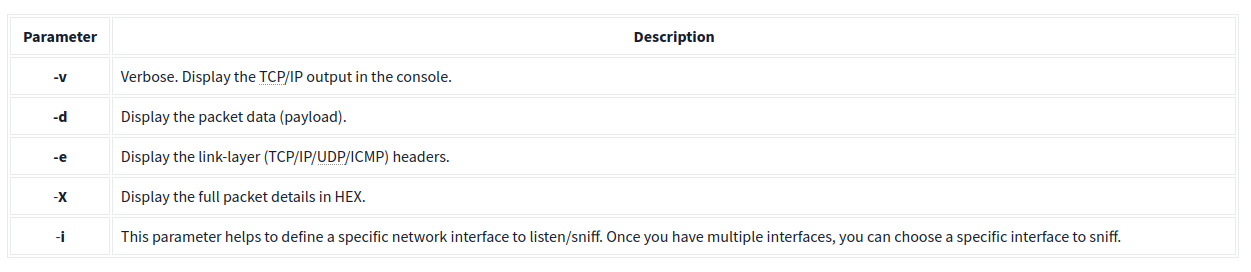
Packet Logger Mode
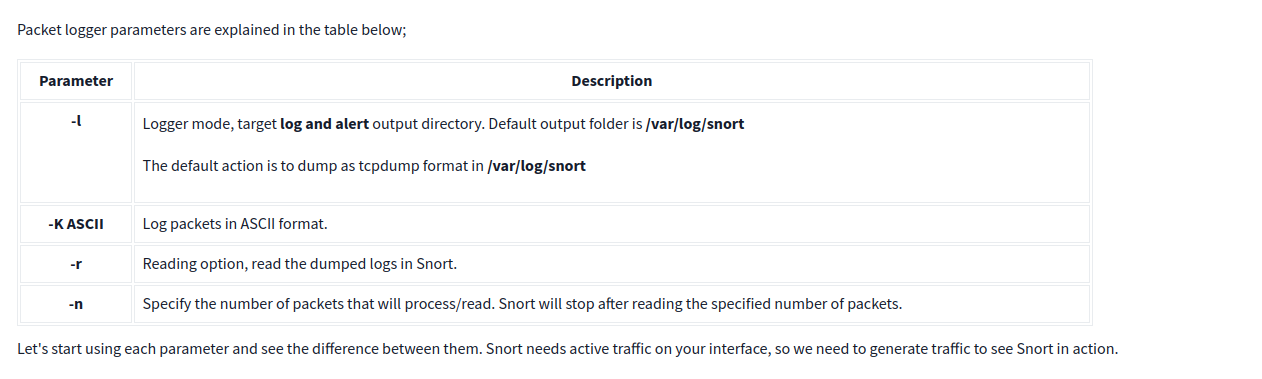
Investigate the traffic with the default configuration file with ASCII mode.
sudo snort -dev -K ASCII -l .
IDS/IPS Mode
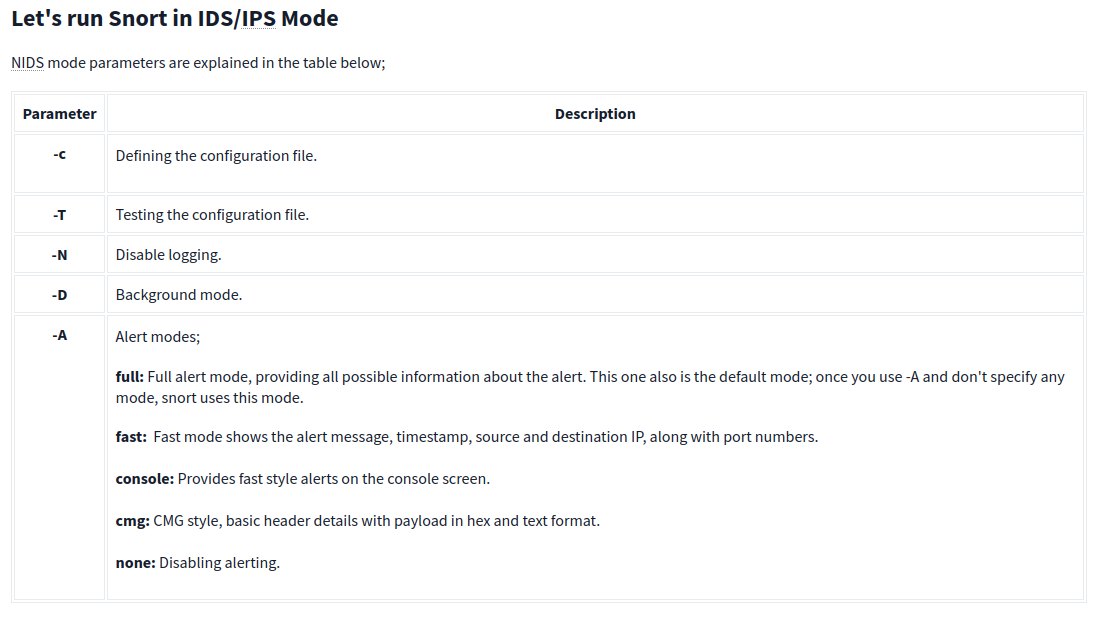
Once you start running IDS/IPS mode, you need to use rules. We will use a pre-defined ICMP rule as an example. The defined rule will only generate alerts in any direction of ICMP packet activity.
alert icmp any any <> any any (msg: "ICMP Packet Found"; sid: 100001; rev:1;)
IDS/IPS mode with the different parameters:
sudo snort -c /etc/snort/snort.conf -T
sudo snort -c /etc/snort/snort.conf -N
sudo snort -c /etc/snort/snort.conf -D
sudo snort -c /etc/snort/snort.conf -D -X -l .
sudo snort -c /etc/snort/snort.conf -A console
sudo snort -c /etc/snort/snort.conf -A cmg
sudo snort -c /etc/snort/snort.conf -A fast
sudo snort -c /etc/snort/snort.conf -A full
sudo snort -c /etc/snort/snort.conf -A none
With parameter “-D”, we can activate verbosity (-v) or full packet dump (-X) with packet logger mode (-l) and we will still have the logs in the logs folder, but there will be no output in the console.
Once you start the background mode and want to check the corresponding process, you can easily use the “ps” command as shown below;
ps -ef | grep snort
If you want to stop the daemon, you can easily use the “kill” command to stop the process.
sudo kill -9 <pid>
Using rule file without configuration file
sudo snort -c /etc/snort/rules/local.rules -A console
IPS mode and dropping packets
Snort IPS mode activated with -Q — daq afpacket parameters. You can also activate this mode by editing snort.conf file.
Activate the Data Acquisition (DAQ) modules and use the afpacket module to use snort as an IPS: -i eth0:eth1
sudo snort -c /etc/snort/snort.conf -q -Q --daq afpacket -i eth0:eth1 -A console
Investigate the traffic with the default configuration file.
sudo snort -c /etc/snort/snort.conf -A full -l .
PCAP Investigation Mode
PCAP read/investigate mode helps us work with pcap files. Once we have a pcap file and process it with Snort, we will receive default traffic statistics with alerts depending on our rule set.
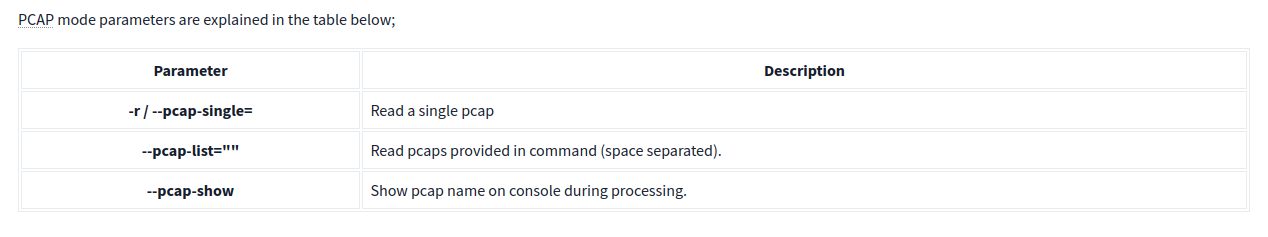
Investigating single pcap file with a configuration file.
sudo snort -c /etc/snort/snort.conf -q -r icmp-test.pcap -A console -n 10
Investigating multiple PCAPs with parameter “ — pcap-list”
sudo snort -c /etc/snort/snort.conf -q --pcap-list="icmp-test.pcap http2.pcap" -A console -n 10
Investigating multiple PCAPs with parameter “ — pcap-show”
Snort will identify the traffic, distinguish each pcap file and prompts the alerts according to our ruleset.
sudo snort -c /etc/snort/snort.conf -q --pcap-list="icmp-test.pcap http2.pcap" -A console --pcap-show