Hacker
A hacker is an individual who uses computer, networking or other skills to overcome a technical problem. The word has been used over the years to refer to anyone who uses their abilities to gain unauthorised access to systems or networks in order to commit crimes. A hacker may, for example, steal information to hurt people via identity theft or bring down a system and, often, hold it hostage in order to collect a ransom.
In case you were wondering where the word ‘hack’ came from… it has been around for a long time, since April 1955 in fact. It was used in a meeting of the MIT Tech Model Railroad Club.
Minutes taken from that meeting read: “Mr. Eccles requests that anyone working or hacking on the electrical system turn the power off to avoid fuse blowing”.
The students at the college are also credited with shifting the term from model railways to computers in the 1960s.
Nation State Actors
Nation State Actors work for governments to disrupt or compromise other target governments, organisations or individuals to gain access to intelligence or valuable data. They have been known to create significant international incidents.
Generally speaking they can operate without fear of legal retribution in their home country and are often part of ‘hackers for hire’ companies aligned to the aims of a government or dictatorship.
Cyber Criminals
Cyber Criminals are individuals or teams of people who commit malicious activities on networks and digital systems, with the intention of stealing sensitive organisation data or personal data, and generating profit.
It’s important to note that the distinction between cyber criminals and nation state actors is becoming increasingly blurred.
Hacktivists
Hacktivists generally operate within the social or political sphere, breaking into and causing damage to computer systems and networks. Targets of hacktivists can vary dramatically from things like the Church of Scientology, to pharmaceutical companies and drug dealers.
Hacktivism is a combination of the words ‘Hacking’ and ‘Activism’. One of the most (in)famous hacktivist groups of recent times would have to be Anonymous, and they are well worth doing some reading on.
CIA Triad
‘CIA triad’ stands for Confidentiality, Integrity, and Availability. It is a common model that forms the basis for the development of secure systems.
- Confidentiality - Confidentiality is to do with keeping an organisation’s data private. This often means that only authorised users and processes should be able to access or modify data.
- Integrity - Integrity means that the data can be trusted. It means that it should be maintained in a correct state, kept so that it cannot be messed around with, it should be correct and also needs to be reliable.
- Availability - It’s all well and good maintaining confidentiality and integrity but the data must be available to use. This means keeping systems, networks and devices up and running.
Being aware of these 3 concepts and how they overlap is important and as Stewart mentioned in the video, some organisations may lean more towards Confidentiality whilst others focus more on Availability depending on what their system or platform is being designed to do.
APT1
Mandiant’s APT1 report highlights several key takeaways, including:
- Advanced persistent threats (APTs) are real and pose a significant threat to organisations.
- APT actors are highly organised, well-funded and operate with a long-term perspective.
- APT actors often target specific organisations and industries for extended periods of time.
- APT actors typically exfiltrate data slowly over time, often using encrypted channels to evade detection.
- APT actors may reuse tools, infrastructure, and tactics across multiple attacks, providing opportunities for attribution and tracking.
- APT actors often seek to maintain a persistent presence within an organisation’s network to support ongoing operations.
- APT actors can evade detection for long periods of time by using stealthy techniques and customising their tactics for each target.
- APT actors use a combination of technical and social engineering tactics to compromise organisations.
- Detecting and responding to APT actors requires a multi-faceted approach that includes regular monitoring and auditing of networks, systems, and user activity.
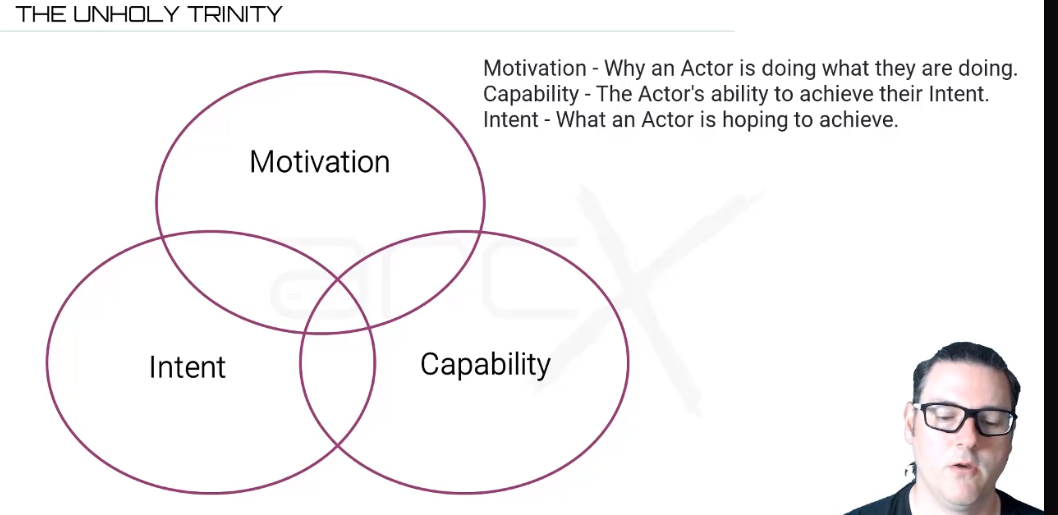
The Unholy Trinity