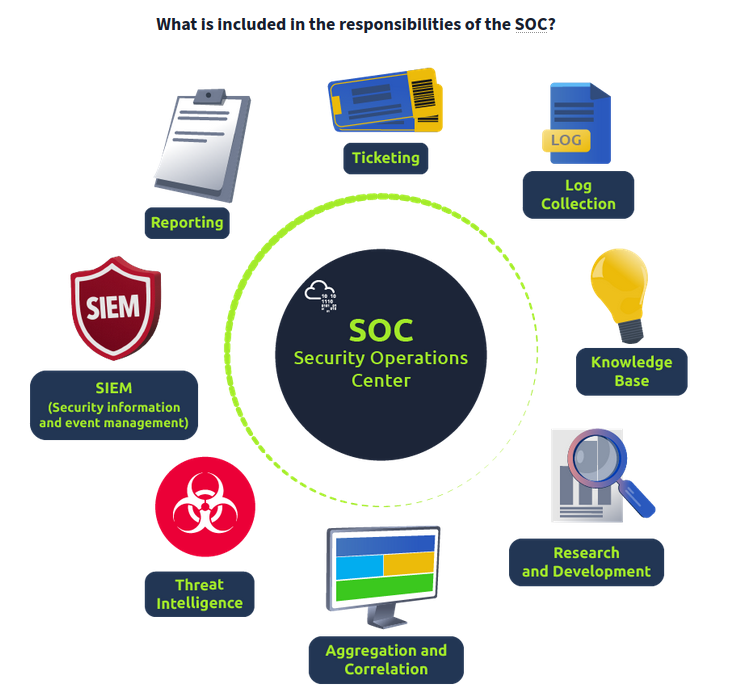
Security Operations Center
Core functions: Investigate, Monitor, Prevent & Respond to threats in Cyber Realm 24/7.
Definition:
Security operations teams are charged with monitoring and protecting many assets, such as intellectual property, personnel data, business systems, and brand integrity. As the implementation component of an organisation's overall cyber security framework, security operations teams act as the central point of collaboration in coordinated efforts to monitor, assess, and defend against cyberattacks”
Preparation: Stay informed of the current cyber security threats. (Twitter & Feedly). Detect and hunt threats, to protect the organisation.
Prevention: Gathering intelligence data on the latest threats, threat actors, and their TTPs (Tactics, Techniques, and Procedures). Maintenance procedures like updating the firewall signatures, patching the vulnerabilities in existing system, block-listing & safe-listing applications, email addresses & IPs.
Monitoring: Uses SIEM (Security Information & Event Management) & EDR (Endpoint Detection & Response) tools to monitor malicious and suspicious network activities.
Note note
As a Security Analyst, you will learn how to prioritise the alerts based on their level: Low, Medium, High, and Critical. Start from the highest level (Critical) and work towards the bottom - Low-level alert. Having properly configured security monitoring tools in place will give you the best chance to mitigate the threat.
Response: After the investigation, the SOC team coordinates and takes action on the compromised hosts, which involves isolating the hosts from the network, terminating the malicious processes, deleting files and more.