YARA
“The pattern matching swiss knife for malware researchers (and everyone else)”
Yara can identify information based on both binary and textual patterns, such as hexadecimal and strings contained within a file.
Rules are used to label these patterns. These YARA rules are used to determine if the file is malicious or not.
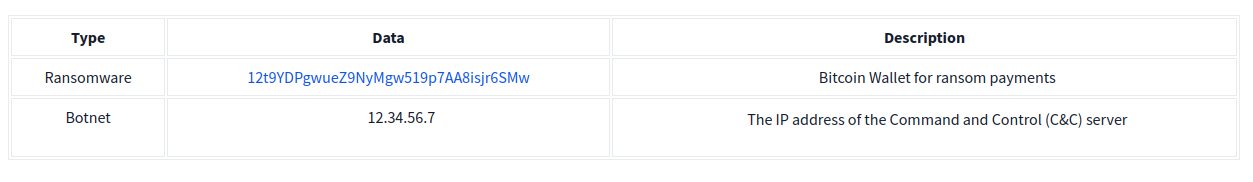
Example: Malware, just like a “Hello World” application, uses strings to store textual data. Here are a few examples of the data that various malware types store within strings:
My First YARA Rule
The proprietary language that Yara uses for rules is fairly trivial to pick up, but hard to master.
Using a Yara rule is simple. Every yara command requires two arguments to be valid, these are:
- The rule file we create. (myrule.yar)
- Name of file, directory, or process ID to use the rule for. (somedirectory) Ex: yara myrule.yar somedirectory
Every rule must have a name and condition. note
STEPS
- Make a file named “somefile” via
touch somefile - Create a new file and name it “myfirstrule.yar” like below:
- Open the “myfirstrule.yar” using a text editor such as
nanoand input the snippet below and save the file:
rule examplerule {
condition: true
}The name of the rule - examplerule
The condition - condition.
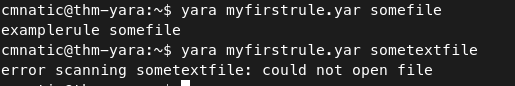 i) In the first command, the file “somefile” exists.
ii) In the second command, the file “sometextfile” does not exist.
i) In the first command, the file “somefile” exists.
ii) In the second command, the file “sometextfile” does not exist.
when the condition met, yara prints the “rule name” & “file name”