YARA Rules
Some Conditions below:
- Meta
- Strings
- Conditions
- Keywords
Meta
Meta condition is like metadata for the yara rule. We can use desc, short for description. It’s like commenting code, to summarize the rule.
Strings
We can use strings to search for specific text or hexadecimal in files or programs. For example, say we wanted to search a directory for all files containing “Hello World!”, we would create a rule such as below:
rule helloworld_checker{
strings:
$hello_world = "Hello World!"
condition:
$hello_world
}- Stored inside the variable $hello_world.
- Condition to check the value in the variable exists.
==Essentially, if any file has the string “Hello World!” then the rule will match. However, this is literally saying that it will only match if “Hello World!” is found and will not match if “hello world” or “HELLO WORLD.”==
To solve this, the condition any of them allows multiple strings to be searched for, like below:
rule helloworld_checker{
strings:
$hello_world = "Hello World!"
$hello_world_lowercase = "hello world"
$hello_world_uppercase = "HELLO WORLD"
condition:
any of them
}Conditions
Some Conditions Operators are:
- ⇐ less than or equal to
- >= more than or equal to
- != not equal to
rule helloworld_checker{
strings:
$hello_world = "Hello World!"
condition:
$hello_world <= 10
}The rule will now:
- Look for the “Hello World!” string
- Only say the rule matches if there are less than or equal to ten occurrences of the “Hello World!” string
Keywords
Some Keywords are:
- and
- not
- or
Checking files which are less than <10 kb and has “Hello World!”
rule helloworld_checker{
strings:
$hello_world = "Hello World!"
condition:
$hello_world and filesize < 10KB
}Anatomy of YARA Rule
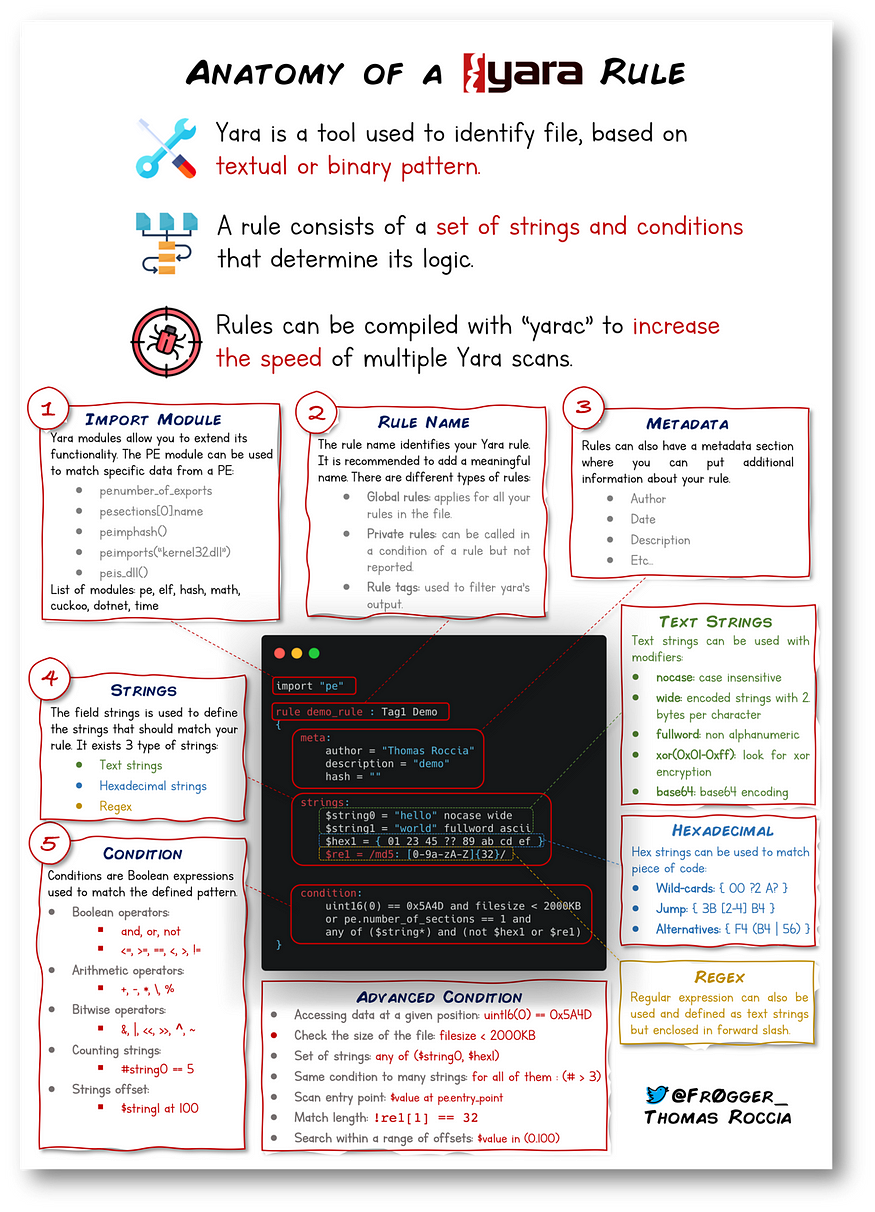
YARA Modules
- Cuckoo Sandbox
- Python PE
Cuckoo
Cuckoo Sandbox is an automated malware analysis environment. This module allows you to generate Yara rules based upon the behaviours discovered from Cuckoo Sandbox. As this environment executes malware, you can create rules on specific behaviours such as runtime strings and the like.
Python PE
Python’s PE module allows you to create Yara rules from the various sections and elements of the Windows Portable Executable (PE) structure.
This structure is the standard formatting of all executables and DLL files on windows. Including the programming libraries that are used.
Examining a PE file’s contents is an essential technique in malware analysis; this is because behaviours such as cryptography or worming can be largely identified without reverse engineering or execution of the sample.