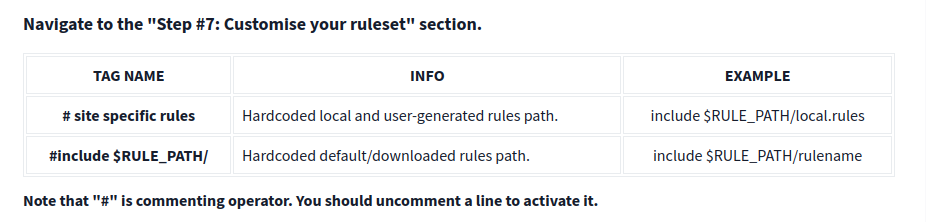
Points to Remember
Snort Cheatsheet - TryHackMe.pdf
Main Components of Snort
- Packet Decoder - Packet collector component of Snort. It collects and prepares the packets for pre-processing.
- Pre-processors - A component that arranges and modifies the packets for the detection engine.
- Detection Engine - The primary component that process, dissect and analyse the packets by applying the rules.
- Logging and Alerting - Log and alert generation component.
- Outputs and Plugins - Output integration modules (i.e. alerts to syslog/mysql) and additional plugin (rule management detection plugins) support is done with this component.
There are three types of rules available for snort
-
Community Rules - Free ruleset under the GPLv2. Publicly accessible, no need for registration.
-
Registered Rules - Free ruleset (requires registration). This ruleset contains subscriber rules with 30 days delay.
-
Subscriber Rules (Paid) - Paid ruleset (requires subscription). This ruleset is the main ruleset and is updated twice a week (Tuesdays and Thursdays).
-
snort.conf: Main configuration file.
-
local.rules: User-generated rules file.

Data Acquisition Modules (DAQ) are specific libraries used for packet I/O, bringing flexibility to process packets. It is possible to select DAQ type and mode for different purposes.
There are six DAQ modules available in Snort;
-
Pcap: Default mode, known as Sniffer mode.
-
Afpacket: Inline mode, known as IPS mode.
-
Ipq: Inline mode on Linux by using Netfilter. It replaces the snort_inline patch.
-
Nfq: Inline mode on Linux.
-
Ipfw: Inline on OpenBSD and FreeBSD by using divert sockets, with the pf and ipfw firewalls.
-
Dump: Testing mode of inline and normalisation.
The most popular modes are the default (pcap) and inline/IPS (Afpacket).